All of the Vigor Router has built-in firewall features which allow Network Administrator to control the incoming and outgoing traffic of the network, thus to enhance the network security, and also prevent network resources being wasted on inappropriate applications. Vigor Router offers a comprehensive firewall: IP-based policies are for controlling the access of traffic from a particular source or to a specific destination, CSM (content security management) for restricting the use of apps or access to websites, and there's also DoS defense to protect the network from flooding attacks. This article is going to give you an overview of how to use the DrayTek firewall.
Contents
- Firewall Rules of Vigor Router
- Filter Set & Filter Rules
- Filter Rule Configuration
- Content Security Management (CSM)
- DoS Defense
Firewall Rules of Vigor Router
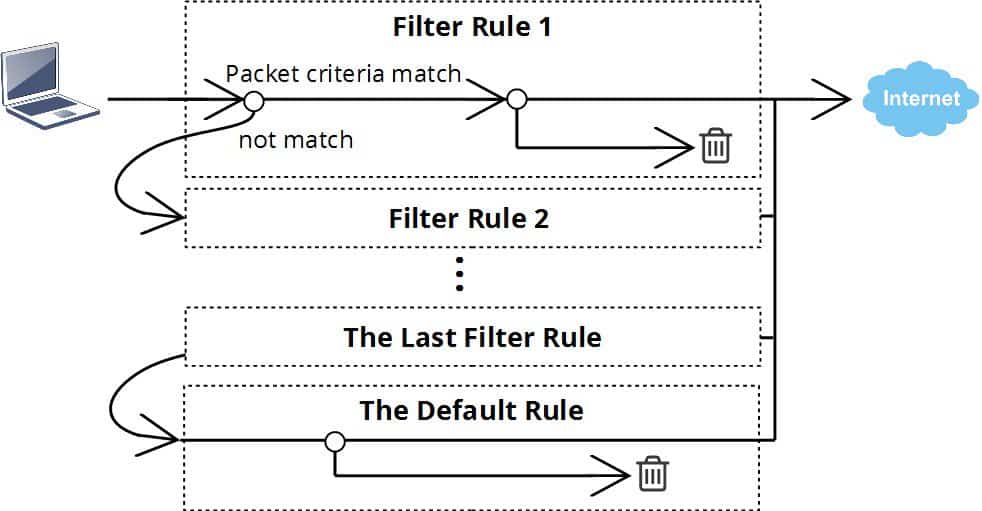
On Vigor Router, we can have more than 80 firewall rules, each of them will apply to the packets that match the filtering conditions of it, which can be direction, source IP address, destination IP address, port number, or/and protocol. The sequence of the firewall rule matters because a packet will only follow one rule. If there is more than one rule matches the criteria of a packet, the rule with the smallest index number will take effect.
If the packet does not match any of the criteria in all the filter rules, it will follow the default rule, which is “pass” in the factory default configuration. The default policy can be changed at Firewall >> General Setup >> “Default Rule” Tab.
Filter Set & Filter Rules
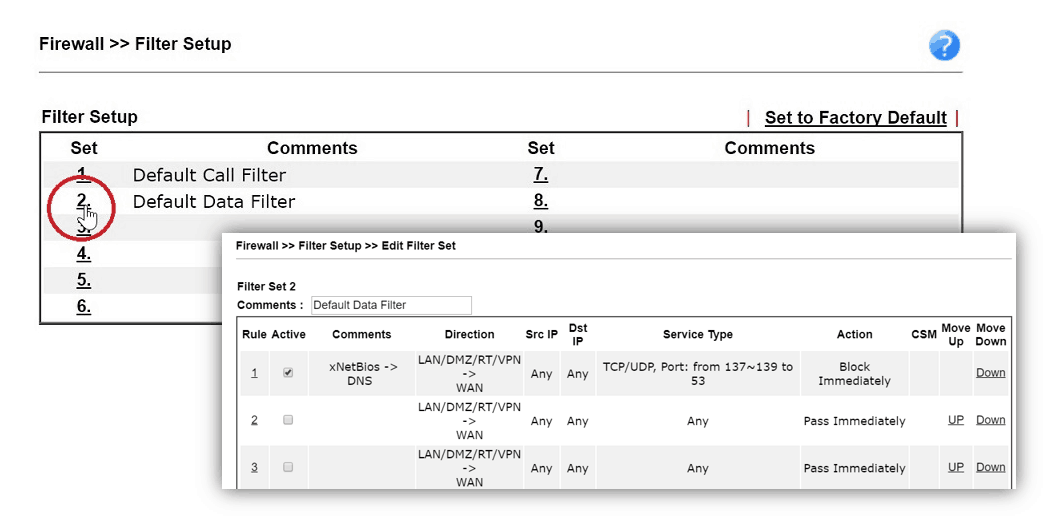
On Firewall >> Filter Setup page, we will see 12 Filter Sets, and each of them contains seven filter rules. By default, Filter Set 1 is used for “Call Filtering”, which means the filter rules in Filter Set 1 will only be active when there is no Internet connection established, and they will only apply to the outgoing packets, this can be used to restricts the traffic which will dial up a WAN connection. Filter Set 2 is the default Data Filter which applies to the general cases.
To add a general filter rule, go to Firewall >> Filter Setup, click on Set 2 to enter the default Data Filter Set. In Filter set 2, you will see there are seven filter rules. Rule 1 is a pre-defined rule to block the outgoing NetBIOS traffic, and we usually start filter configuration from rule number 2.
Filter Rule Configuration
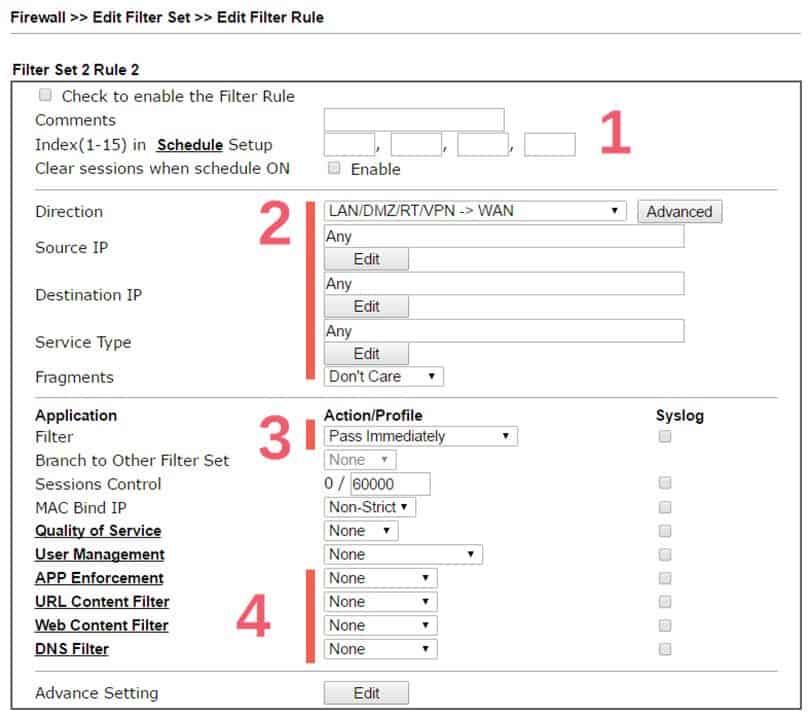
By clicking on the index number, we will enter the rule configuration page. The configuration can be divided into four parts. On the top is where we can give some comments about the rule for identification, and bind this rule with schedule profiles so it will only take effect at a certain time (which is optional).
The second part is the filtering conditions. It defines which packet should follow this rule. Here we may set up one or more conditions, leaving it as “Any” will make this rule apply to all the packets. For example, to set a policy for a specific LAN host, the Direction should be “LAN/DMZ/RT/VPN -> WAN,” and the Source IP should be the LAN IP address of that LAN host.
The third part is the Action of this filter rule. It can either be “block” or “pass.” By choosing “block,” the router will discard all the packets that match the above criteria. If it is “pass,” the router will accept those packets. However, we can still apply application filters to do a content inspection of the packet and then decide to discard the packet if it contains specific information in its data.
Finally, is the Content Security Management (CSM) profiles. These are the application filters that allows the Network Administrator to control the LAN clients’ access to certain websites or restrict usage of certain apps. The following paragraph will describe the difference between them.
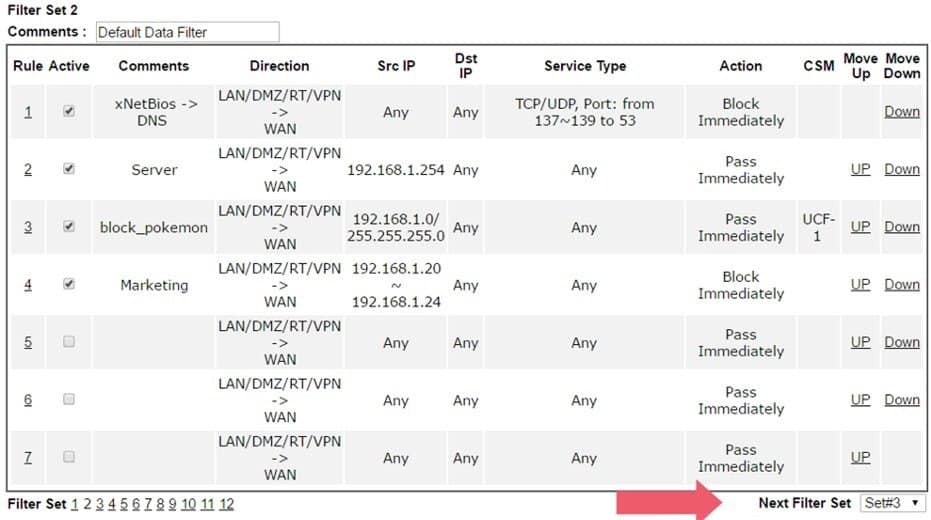
After you use up all the filter rules in Filter Set 2, you may specify the Next Data Filter Set at the bottom of the page, then have more filter rules in the Filter Set selected.
Content Security Management (CSM)
At the bottom of a filter rule configuration, there are four options, APP Enforcement, URL Content Filter, Web Content Filter, and DNS Filter. These together are called Content Security Management (CSM).
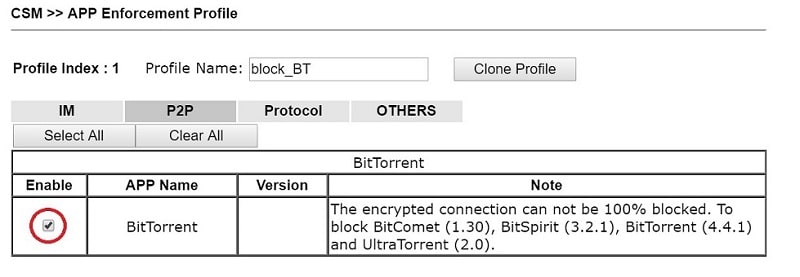
APP Enforcement is for controlling the use of apps. By tracing the packet patterns, the router can recognize the apps that the LAN clients are using, and the Network Administrator can set up policies to block the use of certain apps. The below example is a profile to prevent the use of BitTorrent. See Block Facebook by APP Enforcement for detailed instructions.
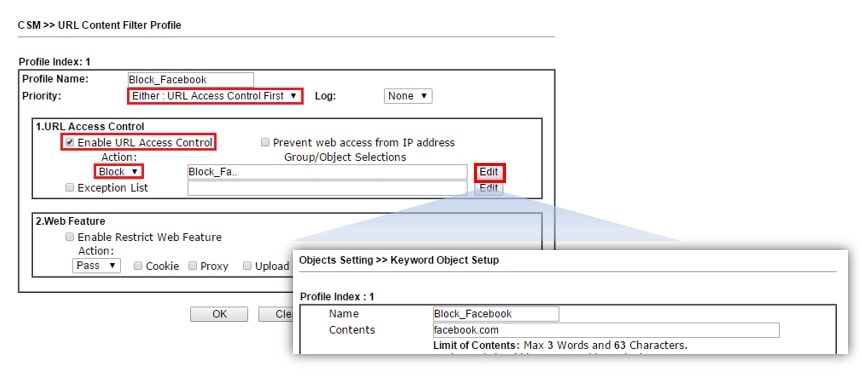
URL Content Filter is for filtering websites. By checking the hostname in the HTTP packets, the router can find out to which site the LAN clients are trying to access. URL Content Filter can either be used as a blacklist, to block the access to a particular URL; or be used as a white list, to pass only the some of the allowed URLs. The example below is a profile to block the access to websites of which the URL contains the keyword "facebook.com." See Blocking Windows Updates for an example.
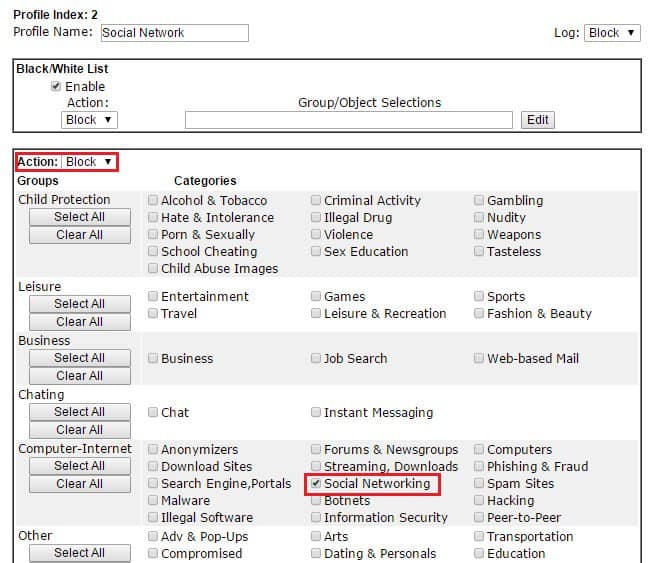
Web Content Filter is also for filtering the websites, however not by URL keyword, but by the category of the websites. It's a license-required service because we are using the URL categorization service from CYREN. The service allows the router to learn which kind of website is the client trying to access, and Network Administrator control the access to all the URLs that fall into a specific category, without specifying each of their URL. The example below is a Web Content Filter profile that will block all the social networking websites. See Block Social Networking Websites by Web Content Filter for detailed instruction.
DNS Filter is an extension of URL Content Filter and Web Content Filter to make sure the HTTPS (encrypted) websites will also be filtered. DNS Filter allows Network Administrator to block or pass the DNS queries that contain specific keywords, thus to control the access to HTTPS websites. See Blocking a Website by URL Content Filter and DNS Filter about creating and applying a DNS Filter profile in Firewall.
DoS Defense
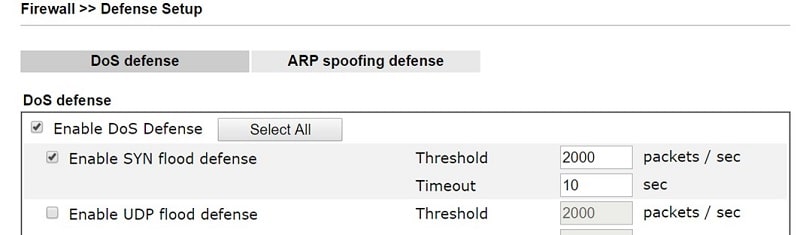
Vigor Router also provides Denial of Service (DoS) Defense to protect the network resources being exhausted by fake connection requests. Network Administrator can enable this from Firewall >> Defense Setup page, and also customize the policy and threshold of each flooding attack.
Published On:2017-08-11
Was this helpful?
