In User-Based management mode, all the LAN client will need to log in with a user account before they can access the Internet. Except for local user accounts, user authentication can also be done by an external authentication server, such as an Active Directory server. This document introduces how to bind the router to an AD/LDAP server and use the server to authenticate the LAN clients.
AD/LDAP Profile Setup
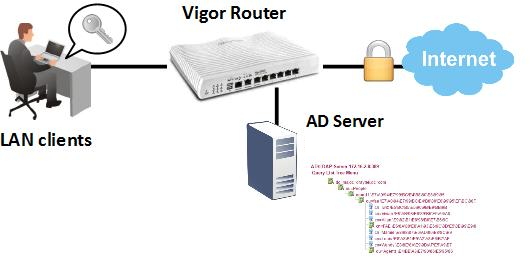
1. Go to Application >> Active Directory/ LDAP >> General Setup, enable AD/LDAP and enter the information of AD/LDAP server as follows:
- Bind Type: Regular Mode
- Server Address: The IP address of AD/LDAP server
- Regular DN: The distinguished name (DN) of administrator account of AD/LDAP server
- Regular Password: The password of the administrator account
- Use SSL: Tick the Use SSL option to secure the LDAP session if the AD/LDAP server supports LDAP over SSL.
2. Click OK to save the configuration, and click OK again when being asked to reboot the router.
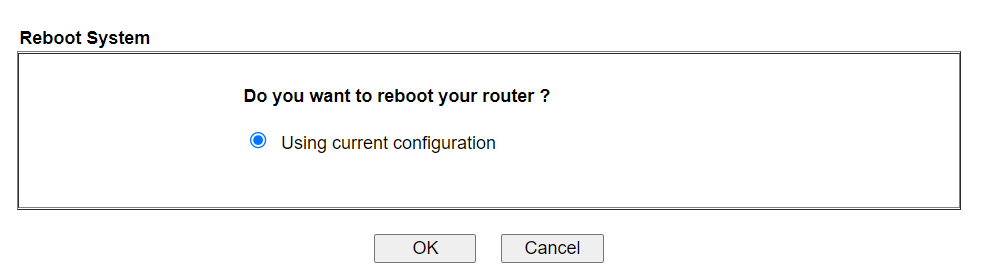
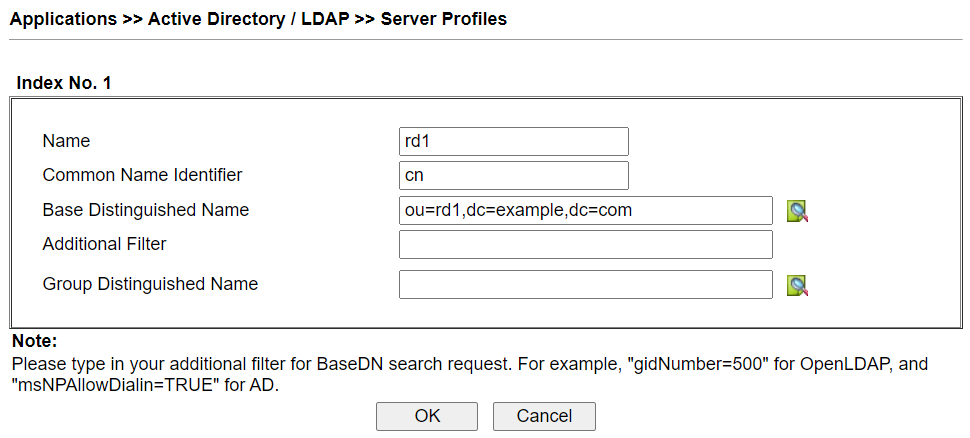
3. Create an AD/LDAP profile: Go to Application >> Active Directory/ LDAP >> AD/LDAP Profiles page, click on an available index number.
4. Edit the profile as follows:
- Give this profile a Name
- Enter the Common Name Identifier that the AD/LDAP server uses (which might be
cnby default) - Enter Base Distinguished Name as the directory from where the router can start searching.
User Management Setup
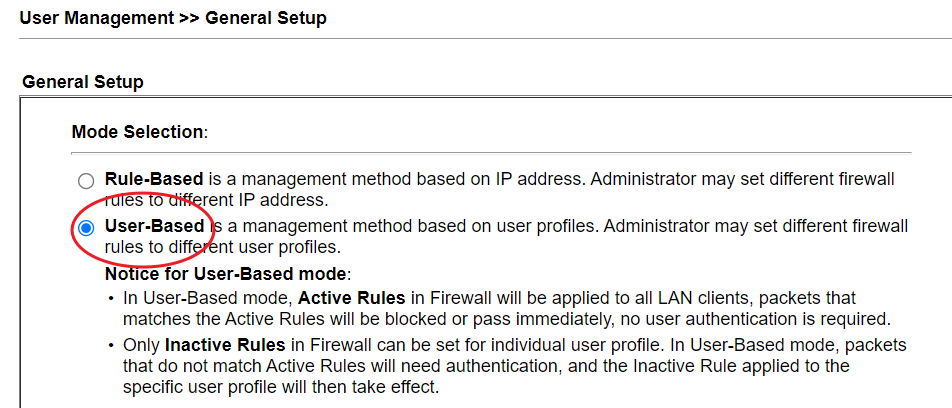
5. Go to User Management >> General Setup to make sure the User Management mode is "User-Based."
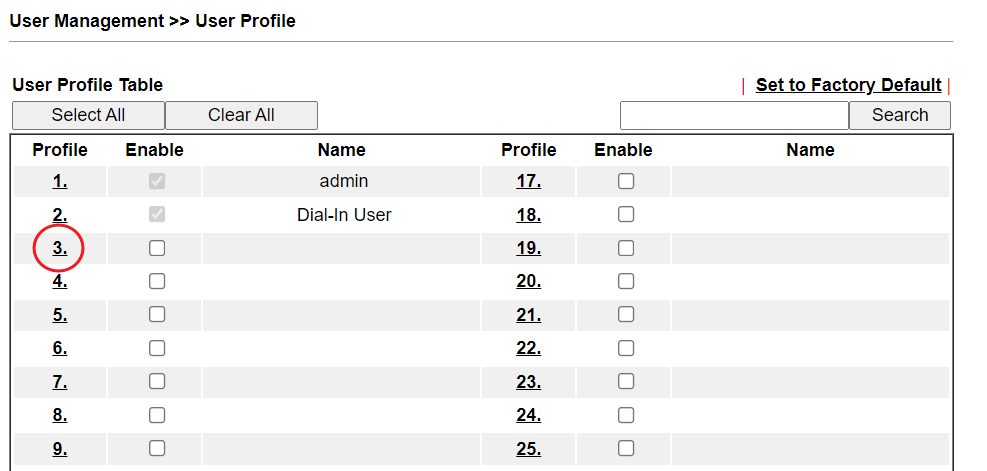
6. Create a new user profile: Go to User Management >> User Profile, click on an available index.
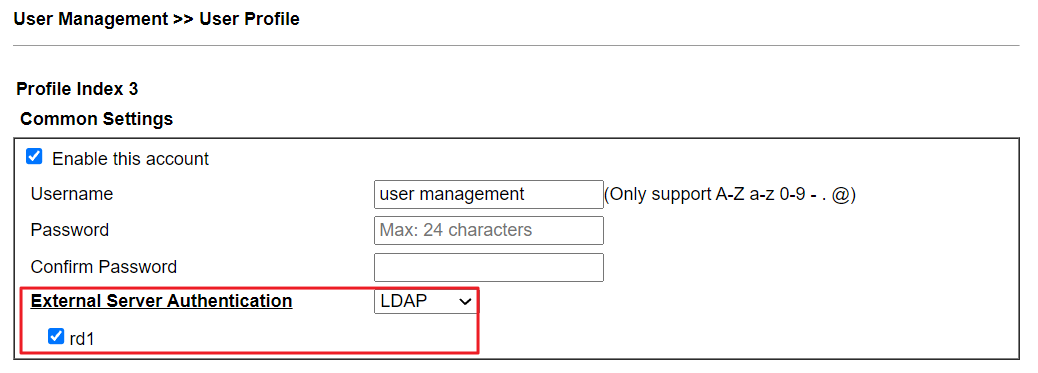
7. Edit the profile as follows:
- Enable this account
- Give it a Username
- At External Server Authentication, select "LDAP" and choose the profile we created in step 3.
- Click OK to save.
User Login
8. Now, when LAN clients access the Internet for the first time, the router will redirect them to a login page. They should log in with a user account on the AD/LDAP database.
9. From User Management >> User Online Status page, Network Administrator will see the users who are authenticated by the AD/LDAP server.
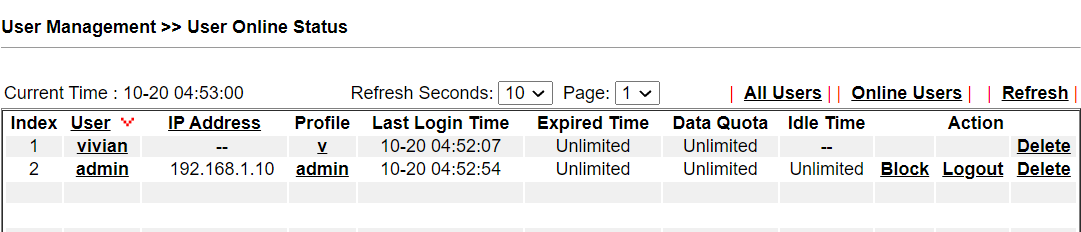
Vigor3900/Vigor2960 supports three binds type for LDAP/AD authentication:
- Simple Mode – Do the bind authentication without any searching.
- Anonymous – Perform anonymous search then do the bind authentication.
- Regular mode – The router is checked by the server to see if it has the search authority first, then it can perform search action and do the bind authentication.
Below we provide examples of using Simple mode and regular mode.
LDAP/AD Setup
1. Navigate to User Management >> LDAP / Active Directory, and click Add to add a new profile.

2. Configure the LDAP profile
(1) Simple mode
Use this mode when the LDAP/AD server has a simple structure. For example, the LDAP/AD server has only one default user group "Users" under the domain "ms.draytek.com," and all the user accounts are under this group. Then we can configure the profile like the following:
- Bind Type: Simple Mode
- Server IP address and Port: the IP of LDAP/AD server and the port to which it is listening.
- Common Name Identifier: cn
- Base DN: cn=Users,dc=ms,dc=draytek,dc=com
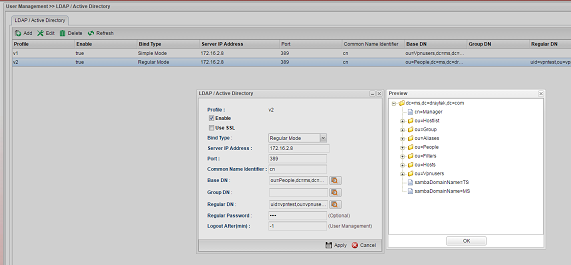
(2) Regular Mode
Use this mode when the LDAP/AD server has multiple levels and required searching to find the path to the user account. For example, there are OU "People" and "Group" under the domain, OU "RD1", "RD2", "RD3" are under the OU "People", OU "MIS", "PQC", "FAE" are under OU "RD1", and we want all the user accounts under OU "People" can be authenticated, then we can configure the profile like the following:
- Bind Type: Regular Mode
- Server IP address and Port: the IP of LDAP/AD server and the port to which it is listening
- Common Name Identifier: cn (Note: "cn" is the recommended settings. If Common Name Identifier is not set as "cn", Vigor Router will send filter with "cn=", "uid=", or "sAMAccountName=" by default)
- Base DN: ou=People,dc=ms,dc=draytek,dc=com
- Regular DN: cn=vivian,cn=vivian,ou=fae,ou=rd1,ou=people,dc=ms,dc=draytek,dc=com (where "vivian" is a user account under OU FAE)
- Regular Password: the password of the account specified in regular DN
In Regular mode, when there is a user authentication request, the router will use the Regular DN and Password to get authenticated by the LDAP/AD server first (a.k.a. simple bind request). After the authentication succeeded, the router will send a search request and see if there is the user account is under Base DN. If LDAP server replies Entry 0, it means the user account doesn't exist in the Base DN. If the user account exists, the LDAP server will respond with the Entry/Path. With the path, the router will send the bind request to the LDAP server for authenticating the user account.
After the configuration, we can verify LDAP by "Preview."
Use Users Management with LDAP/AD
1. Go to User Management >> Web Portal >> General Setup
- Enable Web Portal
- Select a Login mode
- Select LDAP for Authentication Type
- Select the LDAP Profile created in User Management >> LDAP / Active Directory
- Click Apply to finish the setup
2. Now when LAN clients open a browser and access the Internet for the first time, there will be a login page. LAN clients can log in with the user account on LDAP/AD server, and access the Internet after login successfully.
Published On: 2017-11-07
Was this helpful?
