Zero Trust is a strategic approach to security that protects networks by the principle “never trust, always verify.” Instead of assuming everything behind the firewall is safe, the Zero Trust model verifies each request as though it originates from a local network. In other words, servers are in a protected area, all the users need to be authorized or verified first. Therefore we can use the VPN feature Vigor3910 offers to achieve the demand.
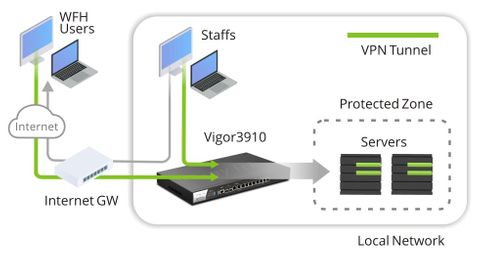
In this scenario, 3910 is located under the Internet gateway, local staffs use the Internet gateway to access Internet. In other words, staffs are on 3910's WAN, so that they can connect VPN to 3910. The Internet gateway also opens VPN ports toward 3910 for WFH users. Alternatively, 3910 can have another WAN interface with public IP for WFH users to connect VPN. The servers are located at 3910 LAN, all the users, staff must connect VPN to Vigor3910 to access them.
Why Vigor3910?
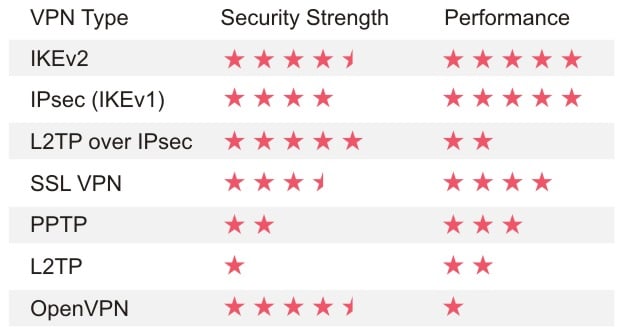
Vigor3910 supports 500 VPN tunnels with high performance and various VPN protocols including SSL VPN, IKEv2 EAP, OpenVPN...etc. Choose the Best VPN Protocol
High secure authentication
A static password is vulnerable to attacks like spyware or phishing. Vigor3910 offers dynamic password MOTP and TOTP for higher security. Dial VPN with mOTP authentication using Windows Smart VPN Client
Deny unauthorized connections
As authentication is the major part of Zero Trust, it’s essential to make sure authentication is secure enough to prevent attacks such as Brute Force, Vigor3910 supports different ways to deny VPN access. Including assigning specific IP for each VPN profile. How to block an unknown IP address which keeps dialing VPN to Vigor Router?
Time oriented VPN control
Another security concern is that VPN service is available anytime, we can set up a schedule for each VPN user of when to connect. Allow VPN Remote Dial-In connections only during Working Hours

Notification for VPN events
Vigor3910 can notify user or network administrator by email once the VPN is up or down, including the source IP. It helps us to detect any misuse of the VPN.
Published On:2021-12-28
Was this helpful?
