As the VPN server, Vigor Router always listens to the VPN ports for accepting VPN connection from on the internet. Sometimes, we may see some unknown IP addresses keep sending VPN request to Vigor Router on Syslog, but cannot find out who the remote peer is. It is annoying and might be a security risk. This document will demonstrate how to block the unknown IP address which keeps dialing VPN to Vigor Router.
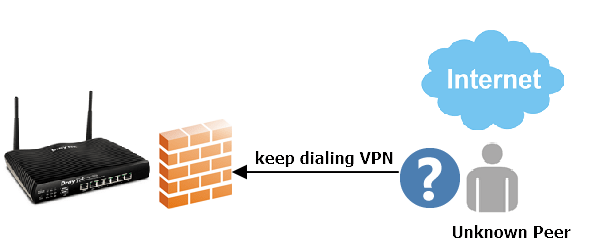
Since firmware 4.4.0, Vigor Router supports the local filter that can be applied for Vigor Router itself. With the local filter, we can block some unknown IP addresses which keep dialing the VPN or keep trying to access the router with the HTTP protocol. Moreover, we can also block IPs from specified countries to prevent the attack by the IP from a specified country. In this article, we demonstrate some practical applications for the local filter.
Application 1: Add the unknown IP into IP Blacklist
- Go to Firewall >> Defense Setup and enable Dos Defense.
- Click White/Black IP List Option.
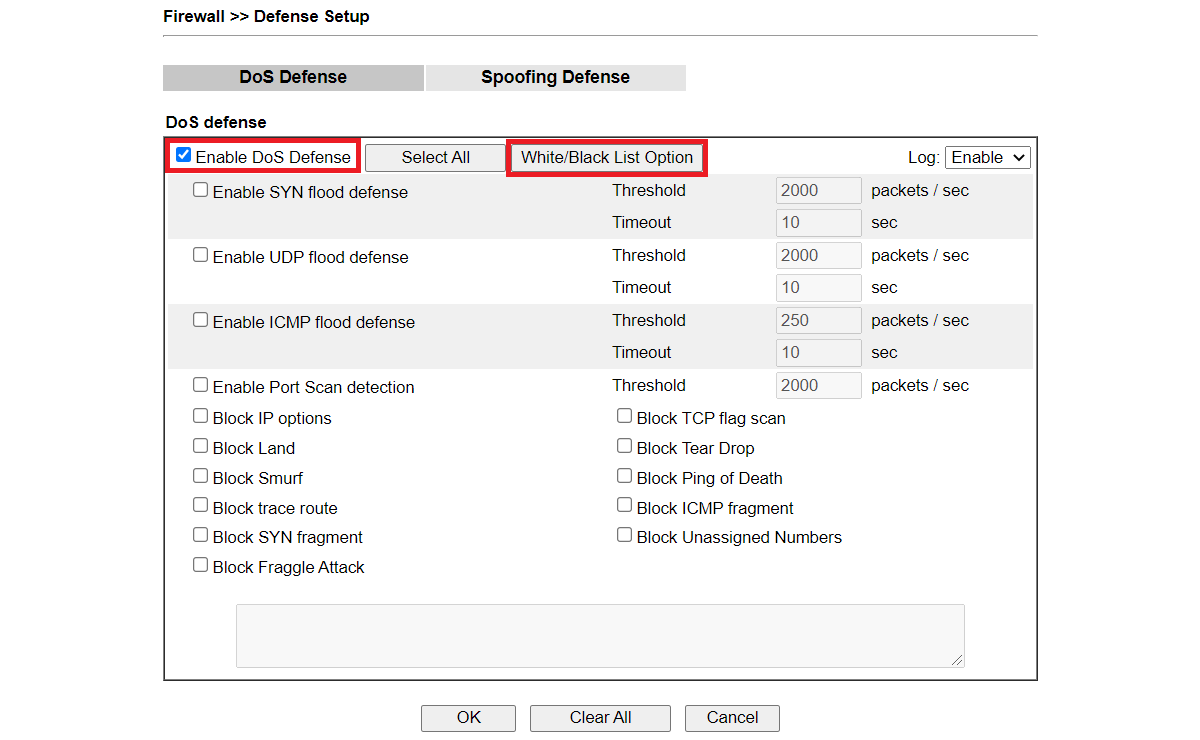
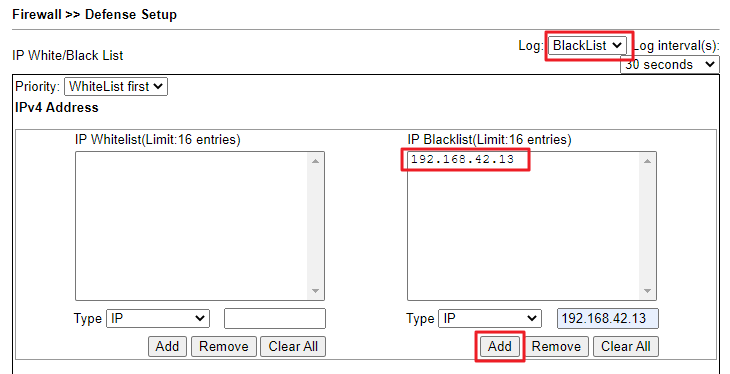
Select log if you want to see from Syslog Explorer.
Input the unknown peer's IP and click Add to add the IP into Black IP List.
| Note: | The Source IP supports 4 options to define IP properties. |
| IP can input single IP address. | |
| IP Object can apply to object profile defined in Objects Setting >> IP Object in advance. | |
| IP Group can apply to group object profile defined in Objects Setting >> IP Group in advance. | |
| Country Object can only apply to object profile defined in Objects Setting >> Country Object in advance. |
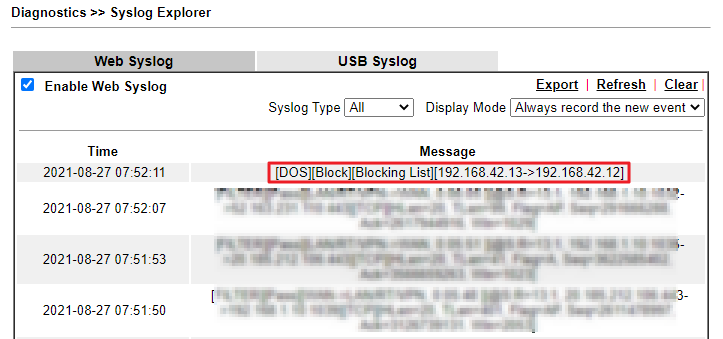
In the Syslog, we will receive an alert from the router when the IP in blacklist attempt to access.
Application 2: Allow the VPN service from a specified country
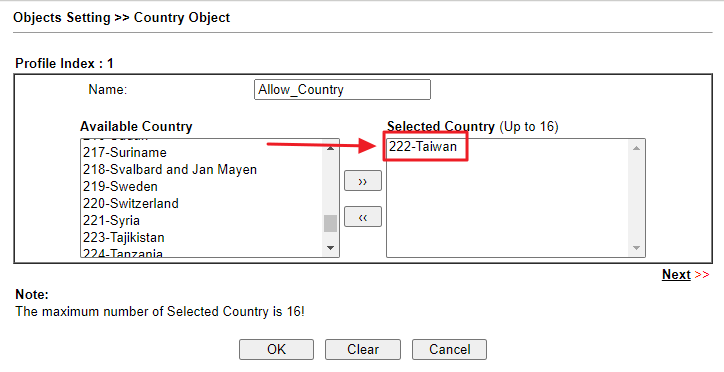
- Go to Objects Setting >> Country Object to create a profile.
- Give a profile name.
- Add the country we would like to allow.
- Click OK to save.
-
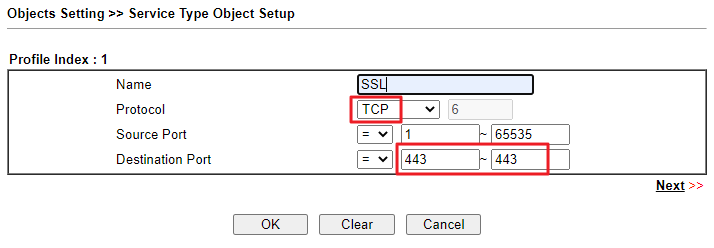
Go to Objects Setting >> Service Type Object to create a profile.
Here we take SSL VPN for example.- Give a profile name.
- Choose the protocol this service uses.
- Enter the port this service would use in Destination Port.
- Click OK to save.
-
Note: Different service uses different service port PPTP -> TCP 1723, GRE(protocol 47) L2TP -> TCP 1701, UDP 500/4500 IPsec -> UDP 500/4500, ESP(protocol 50) SSL -> TCP 443 OpenVPN -> TCP 443/1194, UDP 1194 -
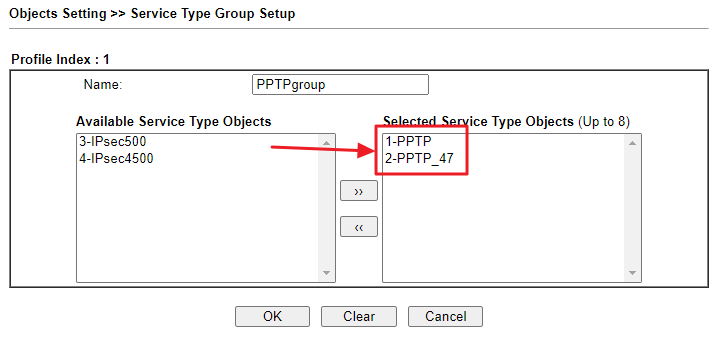
(Optional) If we want to block many services, we can add those service objects into the Service Type Group.
-
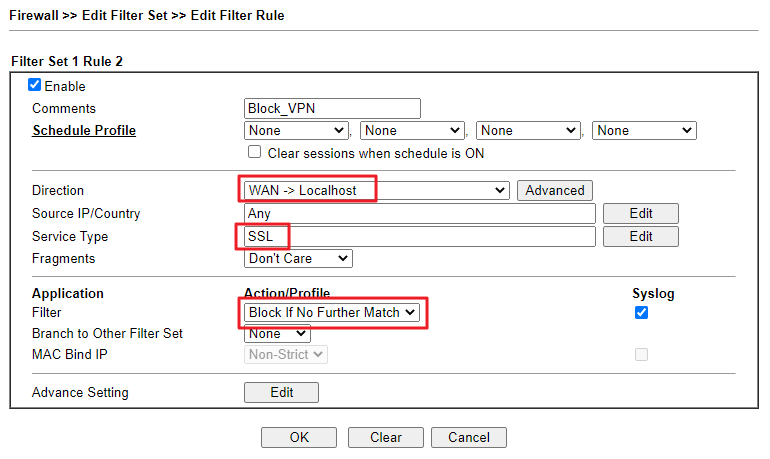
Go to Firewall >> Filter Setup to create a rule that block the VPN service from any Source IP.
- Enable this rule.
- Choose WAN->Localhost for Direction.
- Select Any on Source IP/Country.
- Select the Service Object(or Service Group) created in Step2 on Service Type.
- Choose Block If no further match for Filter. (Check Syslog to show the logs of this rule.)
- Click OK to save.
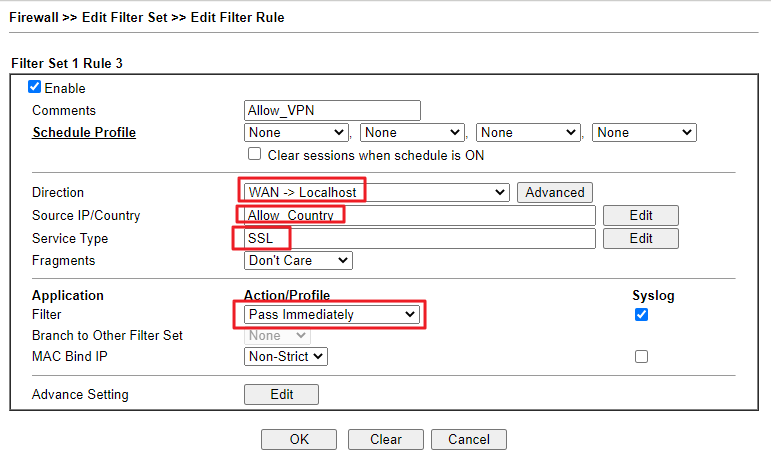
- Create another rule to allow the specified country to use this service.
- Enable this rule.
- Choose WAN->Localhost for Direction.
- Select the Country Object created in step1 on Source IP/Country.
- Select the Service Object(or Service Group) created in Step2 on Service Type.
- Choose Pass Immediately for Filter. (Check Syslog to show the logs of this rule.)
- Click OK to save.
-
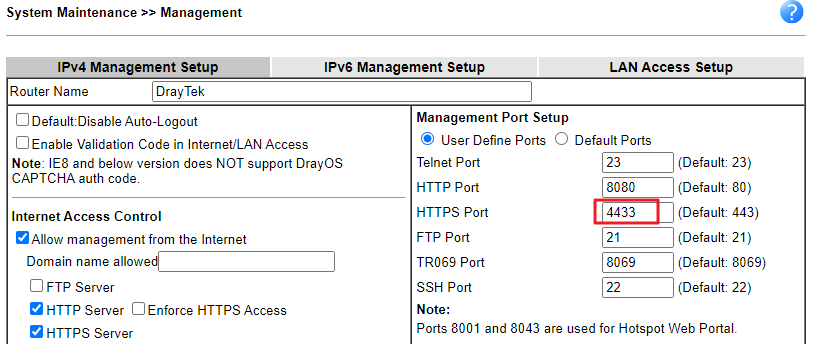
Note: If the service is SSL VPN, please change the HTTPS Management Port of the router. Otherwise, the firewall rule would also block the access of the router's WUI page.
-
In the Syslog, we will see the firewall logs when an IP from this country tries to dial a VPN connection.
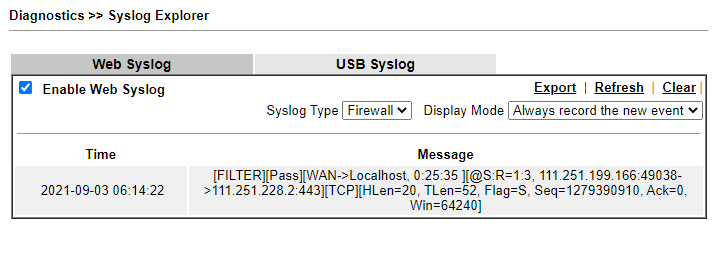
Application 3: Block VPN connection by Brute Force Protection
Vigor Router supports VPN server options in Brute Force Protection which enables users to deny VPN account login attempts from brute-force attack.
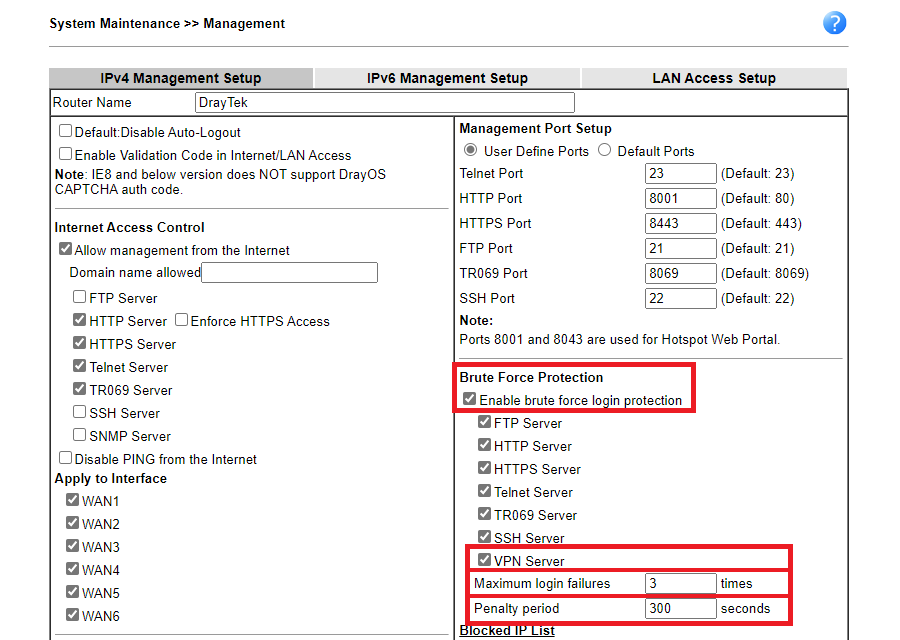
- Go to System Maintenance >> Management to set up Brute Force Protection.
- enable Brute Force Protection.
- select VPN server option.
- setup Maximum login failures from 1 to 255 times.
-
setup Penalty period from 1 to 31536000 seconds(365 days).
-
In the Syslog, we will see firewall logs that peer with the same IP will be denied by Brute Force Protection after it has exceeded maximum login failure time.
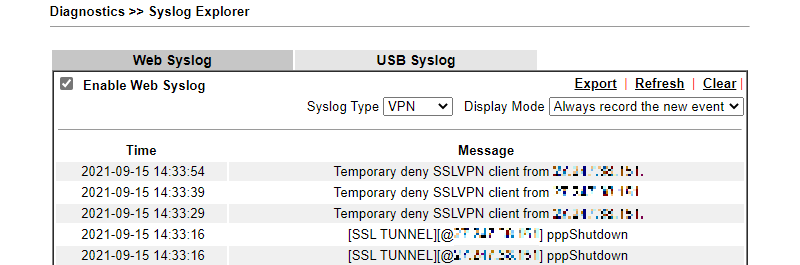
To learn how to use Syslog Utility to collect the syslog, please refer to the article Collecting router's Syslog
Note: DrayTek Routers includes GeoLite2 data created by MaxMind, available from https://www.maxmind.com.
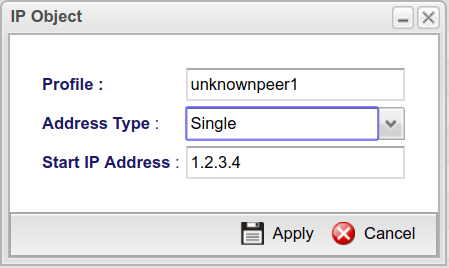
1. Go to Objects Setting >> IP Object page and add the unknown IP as an IP Address.
- Give a profile name.
- Select Single as Address Type.
- Enter the unknown peer IP as Start IP Address.
2. Go to Objects Setting >> Time Object page and add a Time Object.
- Give a profile name.
- Select Weekdays as Frequency.
- Enter Start Time, End Time and Weekdays.
Note: Please enter the Start Time which is later but closed to the current time, and the End Time is a little earlier than the Start Time. For example, if the current time is 15:55 and we can enter the start time as 16:00:00, and the end time as 15:59:59. After the firewall rule effects, this Time Object can be removed.
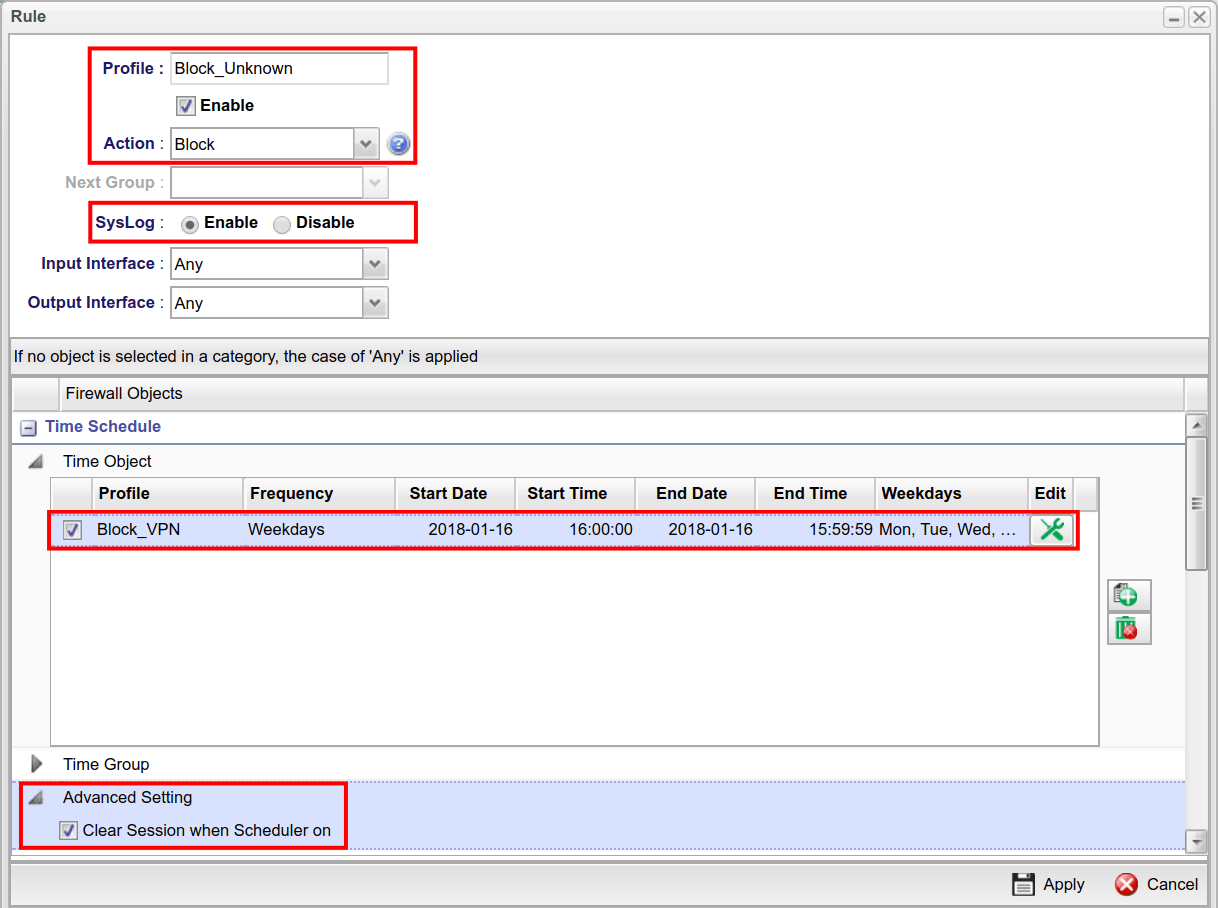
3. Go to Firewall >> Filter Setup page, create an IP Filter Group then click Add to create an IP Filter Rule for blocking the unknown peer IP.
- Check Enable.
- Select Block as Action.
- In Time Schedule >> Time Object, select the Time object created in the previous step.
- In Time Schedule >> Advanced Setting, select Clear Session when Scheduler is on.
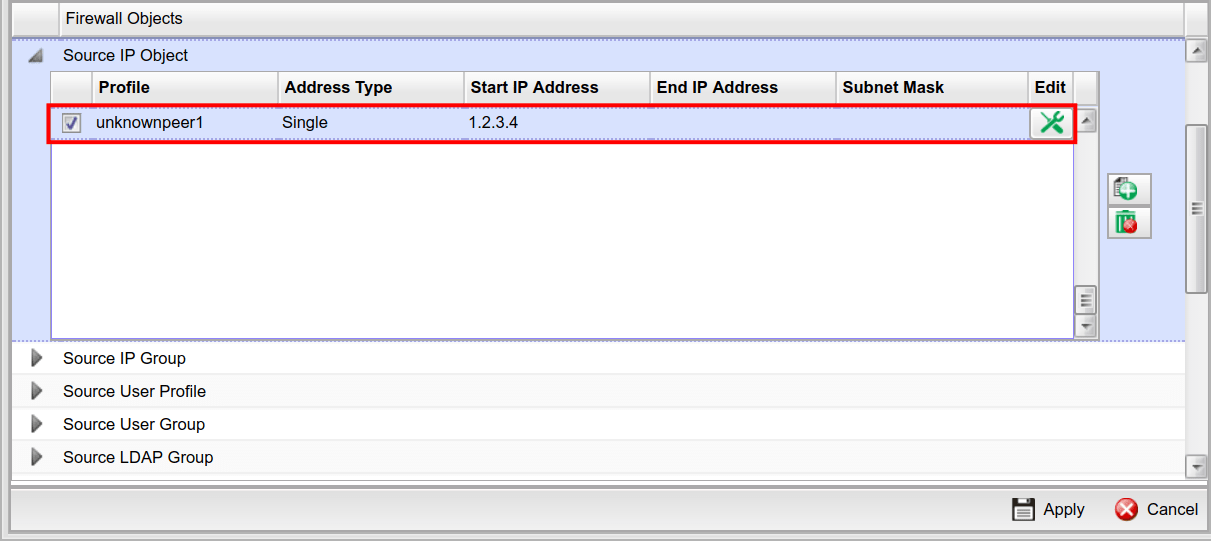
- In Source IP, select the IP object created in the previous step.
- Apply the setting.
After that, we will see such kind of Firewall log instead of the VPN log:
<13>Dec 27 17:13:02 Vigor: [Clear Session] Delete conntrack by ip_filter_set_rule : unknown
<135>Dec 27 17:13:07 Vigor: [IPF-unknown] BLOCK src ip 1.2.3.4 mac 00:1d:aa:xx:xx:xx dst ip 172.17.5.92 proto udp DPT=500, skbmark=10000002/0Published On: 2019-07-08
Was this helpful?
