A Remote Dial-in (also known as Host to LAN) VPN provides a secure connection for a teleworker/VPN client to remotely access a network, for example, in an office. Once the VPN is online, the dial in users can access all of the devices in the network, just like they are physically connected to the LAN. In today's FAE News, we will illustrate how to allow a dial in user to access certain subnet(s) or restrict the user/VPN client to a particular host or subnet with firewall rules.
(For managing LAN-to-LAN VPN users, please refer to this article link.)
Allow a dial in user to access certain subnet(s):
To allow a VPN client to access other subnets, such as LAN2 and LAN3 (fig. 1 shown below), we need to enable “use default gateway on remote network” or "click the More option and enter the subnet(form: xxx.xxx.xxx.0) and the mask you want to access" in the SmartVPN client, and enable inter-LAN routing on VPN Server (in our example, the Vigor router) before establishing the VPN tunnel.
Fig. 1. Allow VPN clients to access other subnet on VPN server when the VPN tunnel has established.
Restrict the user/VPN client to a particular host or subnet with firewall rules:
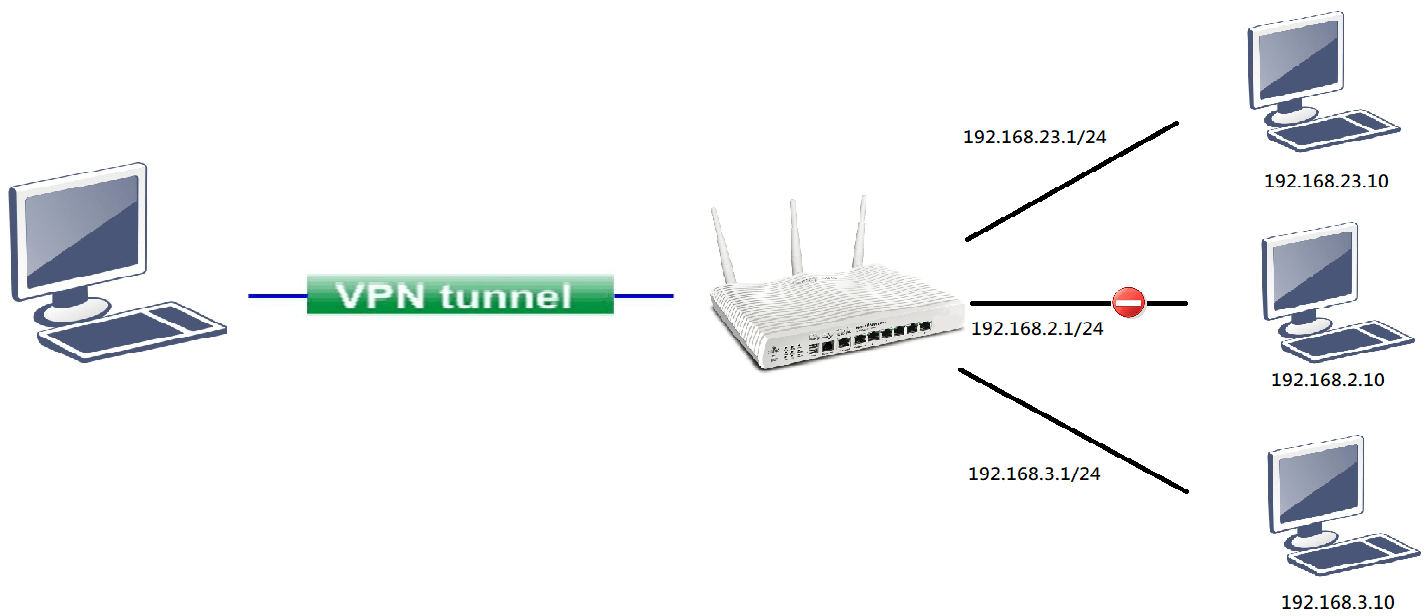
If we want to limit VPN clients to only have access to some specific hosts or subnet, we need to manually assign fixed IP address to these VPN clients(https://www.draytek.com/support/knowledge-base/4812). Then, we can create the firewall rule as in fig.2 below to control the access.
Fig. 2. Assign a fixed IP address of 192.168.23.11 to the dial in user, and then block the IP from accessing subnet 192.168.2.1/24 on VPN server.
Then we can found that the VPN client is blocked when accessing subnet 192.168.2.1/24 in syslog.
Published On:2019-07-23
Was this helpful?
