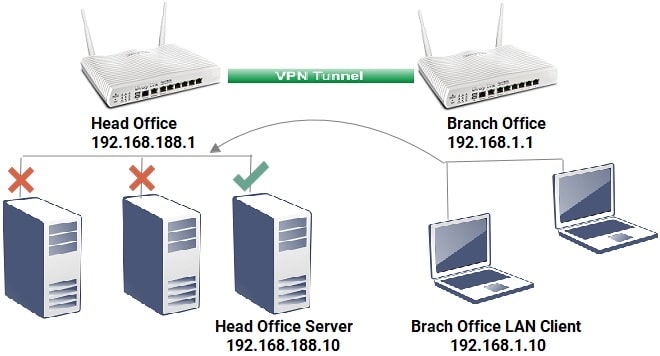
VPN provides a secure connection between local network and remote network. Once VPN is up, the remote network can access all the devices in the local network just as if they are physically connected. But what if we only establish the VPN for the remote network to access a specific server? This article will demonstrate how to configure the router and restrict the remote VPN users to a particular local server only for the scenario below.
There are two ways to achieve this: by VPN configuration and by Firewall rules.
Method 1: By VPN Configuration
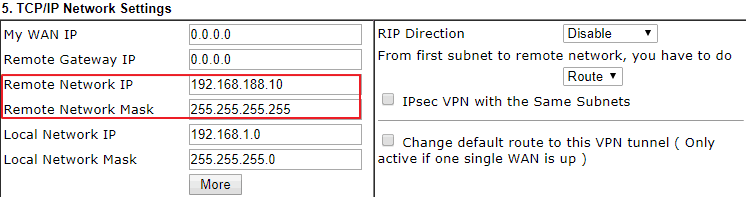
1. In the LAN-to-LAN VPN profile of the Vigor Router in Branch Office, change the Remote Network IP from the whole network to the server's IP only.
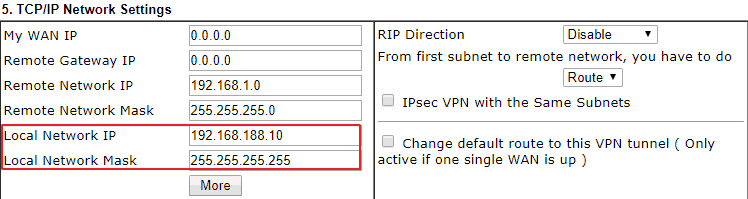
2. On the LAN-to-LAN VPN profile of the Vigor Router in Head Office, change the Local Network IP from the whole network to the server's IP only.
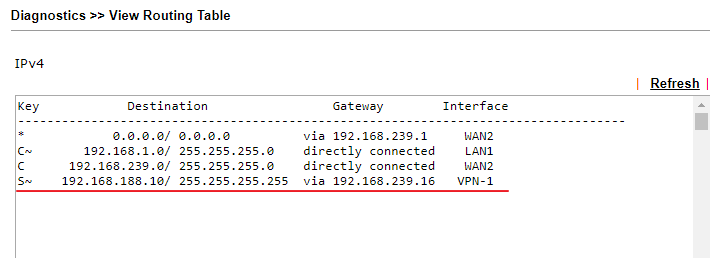
3. When VPN is up, Branch Office Router will only have the routing information to the server's IP 192.168.188.10/32 so that the clients in Branch Office can only access the server.
Method 2: By Firewall Rule
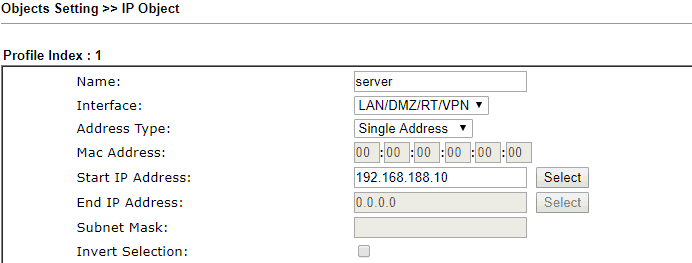
1. We could create the firewall rule in the head office router to limit the connection from the branch office. First, go to Objects Setting >> IP Object, click an available index to create an IP Object profile for the server's IP:
- Enter Name for identifying the object
- Select "LAN/DMZ/RT/VPN" for Interface
- Select "Single Address" for Address Type and then enter the server IP address 192.168.188.10
- Click OK to save
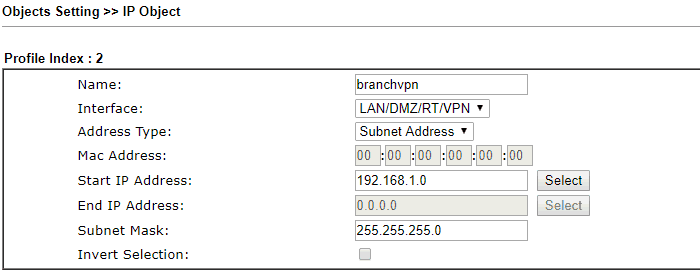
2. Click another available index to create an IP Object profile for the branch VPN network,
- Enter Name
- Select "LAN/DMZ/RT/VPN" for Interface
- Select "Subnet Address" for Address Type and then enter the IP address 192.168.1.0 and Subnet Mask 255.255.255.0
- Click OK to Save
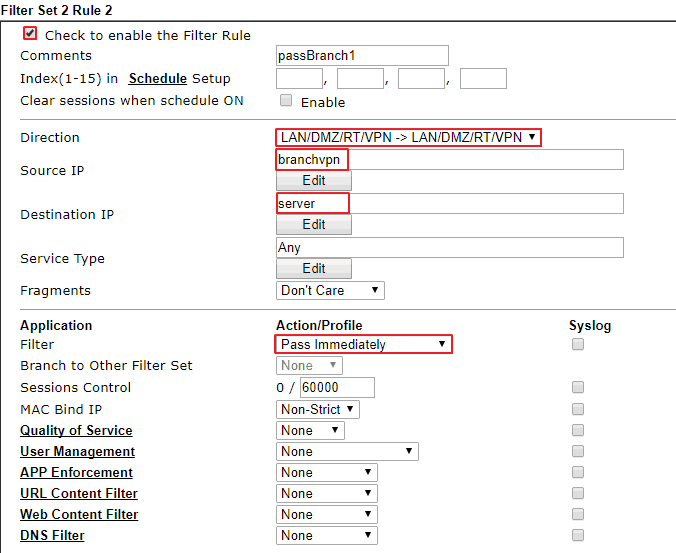
3. Go to Firewall >> Filter Setup >> Filter Set 2 (Default Data Filter), click an available profile to edit the Firewall rule to pass packets from branch office to the server.
- Enable this Firewall rule
- Enter Profile Name
- Direction: LAN/DMZ/RT/VPN → LAN/DMZ/RT/VPN
- Source IP: Select the IP object we created for the branch VPN network
- Destination IP: Select the IP object we created for the local server
- (Optional) Service Type: specify here if we only want the VPN network to access the server on a specific port
- Filter: Pass Immediately
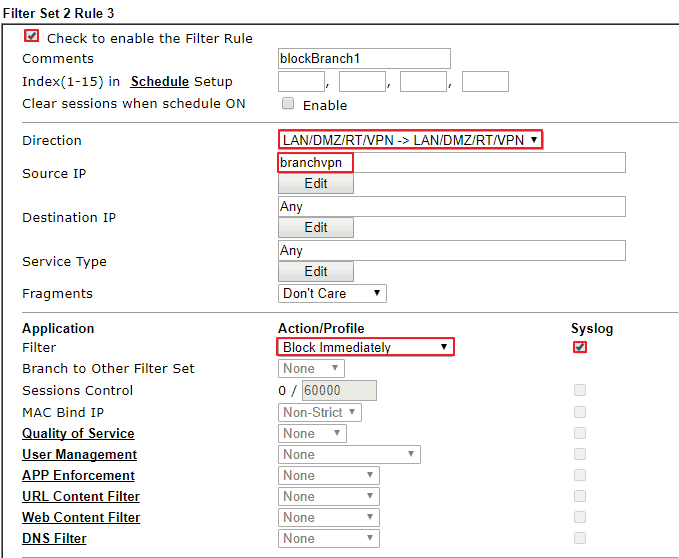
4. Click another Index to create an IP Filter rule (the index number should be larger than the one of step 3) to block packets from the branch office to the other IP addresses.
- Enable this Firewall rule
- Enter Profile Name
- Direction: LAN/DMZ/RT/VPN → LAN/DMZ/RT/VPN
- Source IP: Select the IP object we created for the branch VPN network
- Destination IP: Any
- Filter: Block Immediately
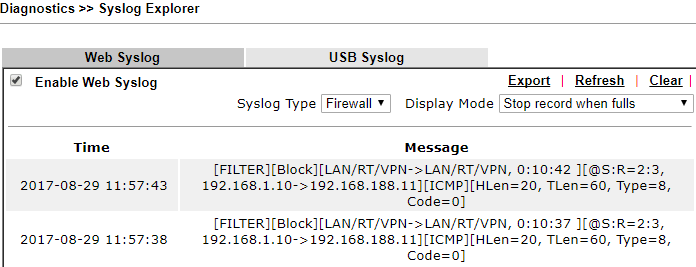
And that is the configuration required. We can check Firewall logs on Diagnostics >> Syslog Explorer page to see if there is traffic being filtered.
There are two ways to achieve this: by VPN configuration and by Firewall rules.
Method 1: By VPN Configuration
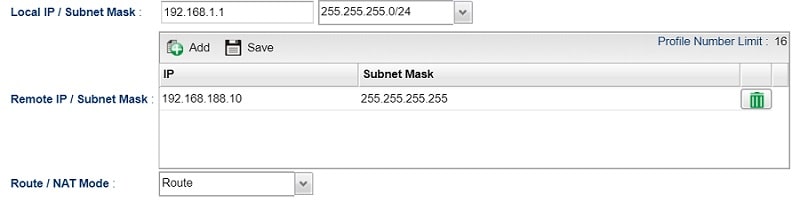
1. In the LAN-to-LAN VPN profile of the Vigor Router in Branch Office, change the Remote IP / Subnet Mask from the whole network to the server's IP only.
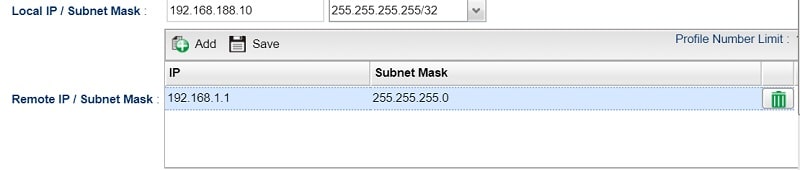
2. On the LAN-to-LAN VPN profile of the Vigor Router in Head Office, change the Local IP / Subnet Mask from the whole network to the server's IP only.
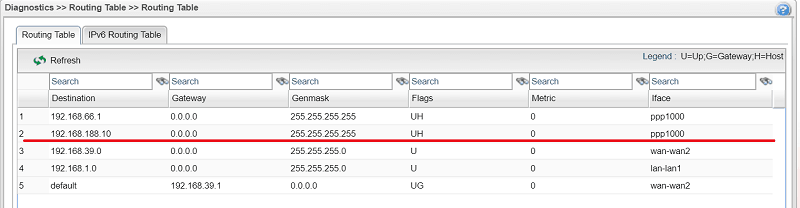
3. When VPN is up, Branch Office Router will only have the routing information to the server's IP 192.168.188.10/32 so that the clients in Branch Office can only access the server.
Method 2: By Firewall Rule
1. We could create the firewall rule in the head office router to limit the connection from the branch office. First, go to Firewall >> Filter Setup >> IP Filter, click Add to create a new group.
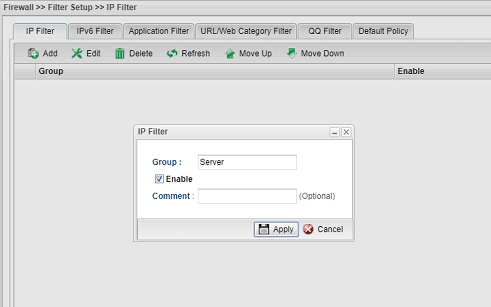
2. In the filter group, add a new rule as follows:
- Enter Profile Name
- Check Enable
- Select "Block if No Further Match" for Action
- In Source IP add an object for Branch Office network and select it
- In Destination IP add an object for Head Office network and select it
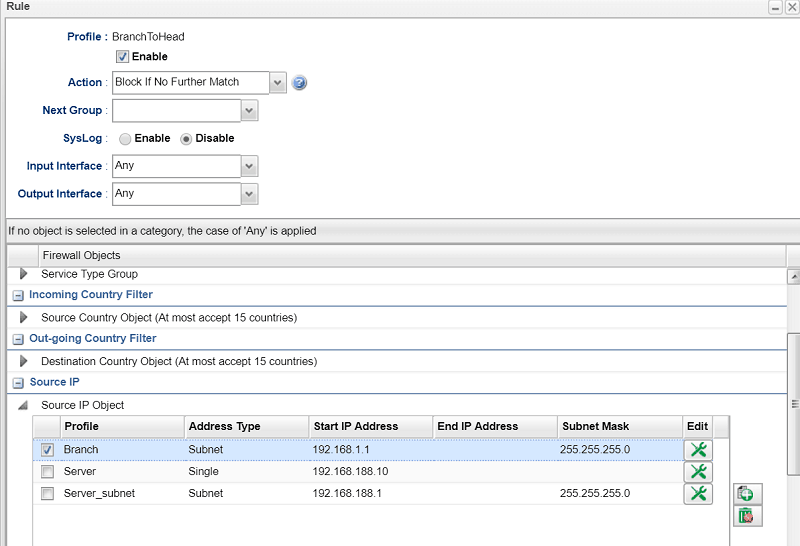
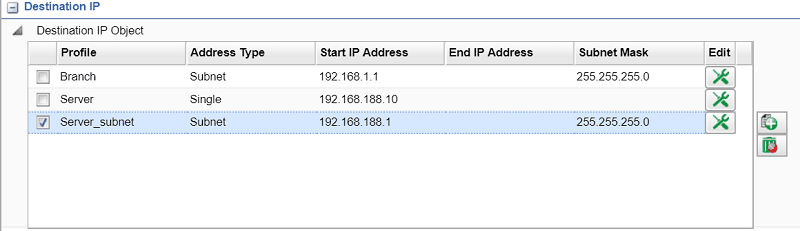
3.Add a second rule as follows:
- Enter Profile Name
- Check Enable
- Select "Accept" for Action
- In Source IP add an object for Branch Office network and select it
- In Destination IP add an object for the Server's IP and select it
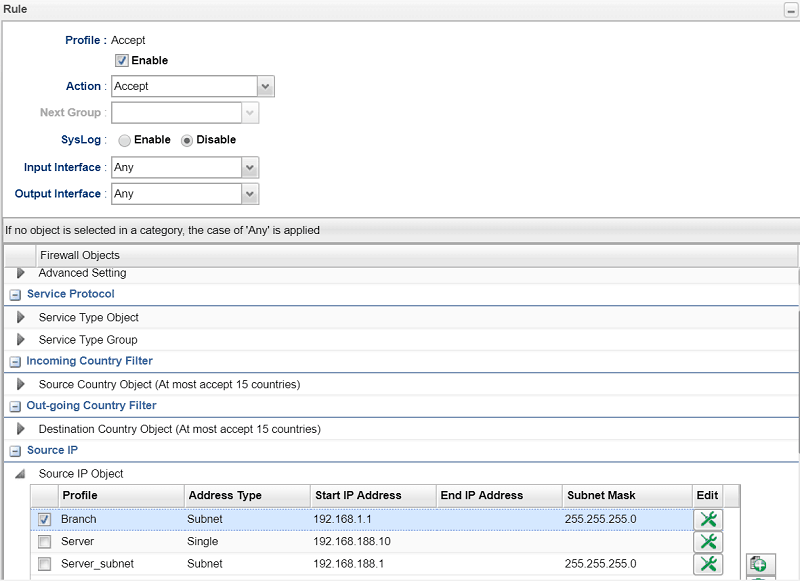
And that is the configuration required.
Published On: 2018-05-02
Was this helpful?
