Vigor Router supports authenticating PPTP/L2TP/SSL Remote Dial-In VPN connections by the local database or external authentication servers, including RADIUS, LDAP/ AD and TACACS+. This article explains the configuration of using an external LDAP/AD server for VPN authentication.
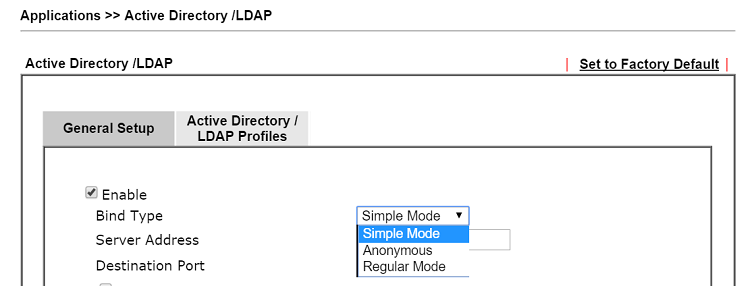
1. Go to Applications >> Active Directory /LDAP. Check Enable and choose a Bind Type. There are three types available:
Simple Mode – It is usually the option when users are all in the same folder/ level in the AD/LDAP server. The router does only the bind authentication but no searching.
Anonymous Mode – Perform a searching action first with Anonymous account, and then do the bind authentication. It is rarely used. In fact, Windows AD server refuses to authenticate Anonymous account by default.
Regular Mode – It is usually the option when users are in different sub-folders. Mostly it is the same with Anonymous Mode, but the server will first check if you have the search authority with Regular DN and
Regular Password authentication. In this mode, the router will send Bind Request with this Regular DN and Regular Password to LDAP/AD server, once it passed the authentication, the router will do searching then LDAP server will find the exact user's DN in different sub-folders.
In this example, we will use Regular Mode. Suppose Draytek LDAP server has OU People and OU RD1, RD2, RD3 under OU People, and the Users under OU RD1, RD2, RD3 are allowed for VPN Access.
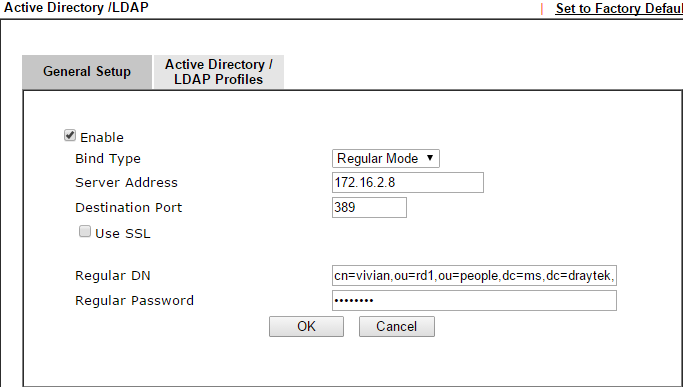
2. Enter the IP address of LDAP/AD server at Server Address, and input Regular DN and Regular Password. Click OK then Vigor will request a system restart
Note: If the LDAP server you have is Windows AD server, always use cn= for the start of Regular DN.
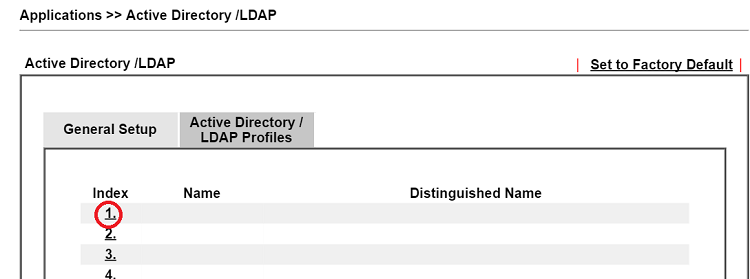
3. Create LDAP server profiles. Go to the Active Directory /LDAP tab click an index number to edit the profile.
4. Enter a Name for the profile. And once the server has authenticated Regular DN/ Password that the router use, we can use the Search icon to input the Base Distinguished Name quickly. In this example, we want to allow users under OU RD1, RD2, and RD3 to access VPN, so we select the OU people that contains OU RD1, RD2, and RD3, for Base Distinguished Name. Then click OK.
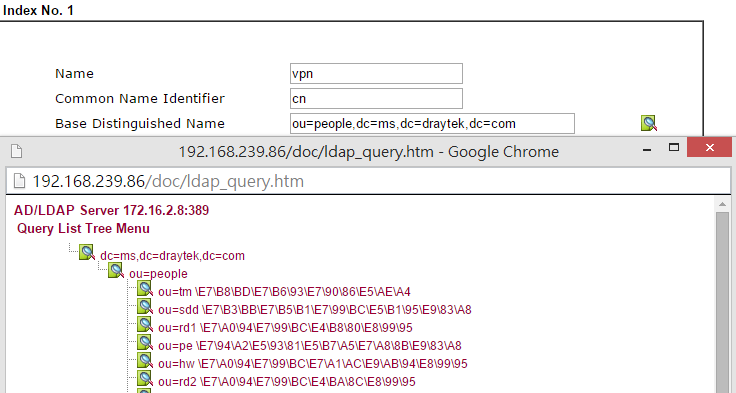
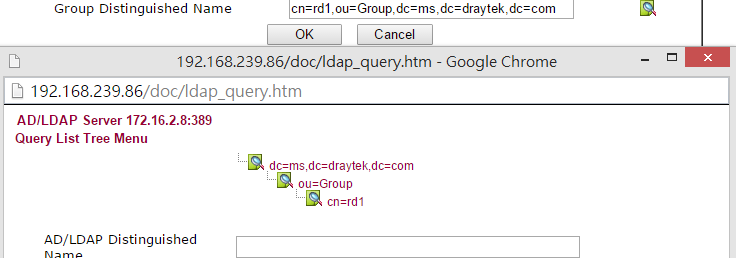
5. (Optional) Group DN for additional filtering. If both Base DN and Group DN are specified, only the users available in both path can pass the authentication.
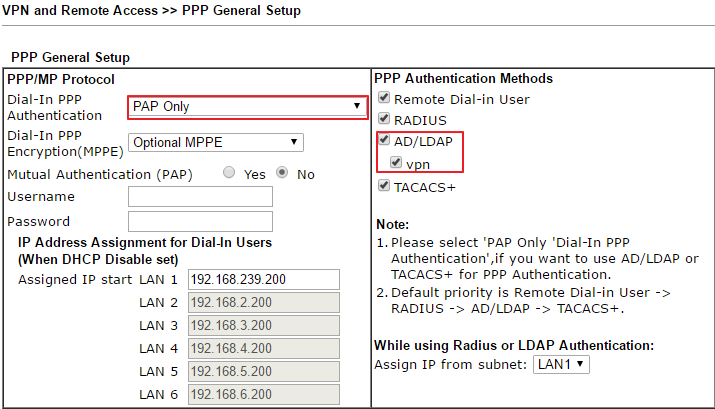
6. Configure the router to authenticate Host-to-LAN VPN with the external server: Go to VPN and Remote Access >> PPP General Setup, at PPP Authentication Methods, enable AD/LDAP and the profile created in the previous steps and select PAP Only as the PPP Dial In Authentication method.
With the above configuration, remote VPN clients will be able to establish VPN with the user accounts in LDAP server.
Note:
- There are 4 PPP Authentication Methods: Remote Dial-In User (the local database), RADIUS, AD/ LDAP, TACACS+. When all of them are enabled the router will first check the local database, if it does not match any, it will forward the authentication information to the RADIUS server. Then the LDAP/ AD server if authentication on RADIUS server fails as well.
- When using LDAP server for authentication, as a limitation of LDAP authentication, we must choose PAP as security protocol in the dialing-in via Smart VPN Client, which will cause PPTP VPN established without encryption; therefore, it is suggested to use RADIUS authentication for higher security.
Troubleshooting
When using Windows AD server for authentication, we may test the bind account "vpn-user" by running ldp.exe. to connect to a Domain Controller of the Windows AD server then perform a Simple Bind on the AD server. If Simple Bind on the AD server works but VPN still cannot pass the AD authentication, please contact our us via [email protected] and provide the information below.
- wireshark packets on the LDAP/AD server
- screenshots of the User account on the AD/ LDAP server
- screenshots of the LDAP/ AD configurations on the router
- Remote management info of the router
- An account/ password on the LDAP/ AD server for testing
Vigor3900/Vigor2960 supports three binds type for LDAP/AD authentication:
- Simple Mode – Do the bind authentication without any searching.
- Anonymous – Perform anonymous search then do the bind authentication.
- Regular mode – The router is checked by the server to see if it has the search authority first, then it can perform search action and do the bind authentication.
Below we provide examples of using Simple mode and regular mode.
LDAP/AD Setup
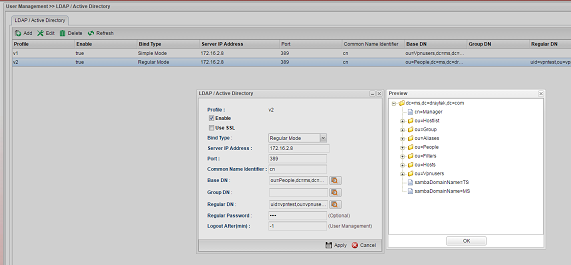
1. Navigate to User Management >> LDAP / Active Directory, and click Add to add a new profile.

2. Configure the LDAP profile
(1) Simple mode
Use this mode when the LDAP/AD server has a simple structure. For example, the LDAP/AD server has only one default user group "Users" under the domain "ms.draytek.com," and all the user accounts are under this group. Then we can configure the profile like the following:
- Bind Type: Simple Mode
- Server IP address and Port: the IP of LDAP/AD server and the port to which it is listening.
- Common Name Identifier: cn
- Base DN: cn=Users,dc=ms,dc=draytek,dc=com
(2) Regular Mode
Use this mode when the LDAP/AD server has multiple levels and required searching to find the path to the user account. For example, there are OU "People" and "Group" under the domain, OU "RD1", "RD2", "RD3" are under the OU "People", OU "MIS", "PQC", "FAE" are under OU "RD1", and we want all the user accounts under OU "People" can be authenticated, then we can configure the profile like the following:
- Bind Type: Regular Mode
- Server IP address and Port: the IP of LDAP/AD server and the port to which it is listening
- Common Name Identifier: cn (Note: "cn" is the recommended settings. If Common Name Identifier is not set as "cn", Vigor Router will send filter with "cn=", "uid=", or "sAMAccountName=" by default)
- Base DN: ou=People,dc=ms,dc=draytek,dc=com
- Regular DN: cn=vivian,cn=vivian,ou=fae,ou=rd1,ou=people,dc=ms,dc=draytek,dc=com (where "vivian" is a user account under OU FAE)
- Regular Password: the password of the account specified in regular DN
In Regular mode, when there is a user authentication request, the router will use the Regular DN and Password to get authenticated by the LDAP/AD server first (a.k.a. simple bind request). After the authentication succeeded, the router will send a search request and see if there is the user account is under Base DN. If LDAP server replies Entry 0, it means the user account doesn't exist in the Base DN. If the user account exists, the LDAP server will respond with the Entry/Path. With the path, the router will send the bind request to the LDAP server for authenticating the user account.
After the configuration, we can verify LDAP by "Preview."
Authenticate Remote Dial-in Client with LDAP/AD
1. After finishing the configuration of LDAP/AD profile, we can use it for Remote Dial-in clients. Navigate to VPN and Remote Access >> PPP General Setup >> PPTP.
- Select LDAP for User Authentication Type
- Select the LDAP profile as the profile configured in step 2.
- Choose the LAN profile which the remote user will join. (Note that if the selected LAN profile does not have DHCP server enabled, we would need to turn on Specify IP for Remote Dial-in option)
2. Here we use Smart VPN Client as a VPN client. Run Smart VPN client, and click Insert to create a new VPN profile, configure the VPN profile as follows:
- Profile name
- Type of VPN: PPTP
- VPN Server IP: The IP address or Hostname of Vigor3900
- User Name and Password: the user account and password in LDAP/AD server
3. In PPTP Setup, choose the Authentication method to "PAP". Click OK to save.
Published On: 2016-05-12
Was this helpful?
