This video was presented by DrayTekUSA
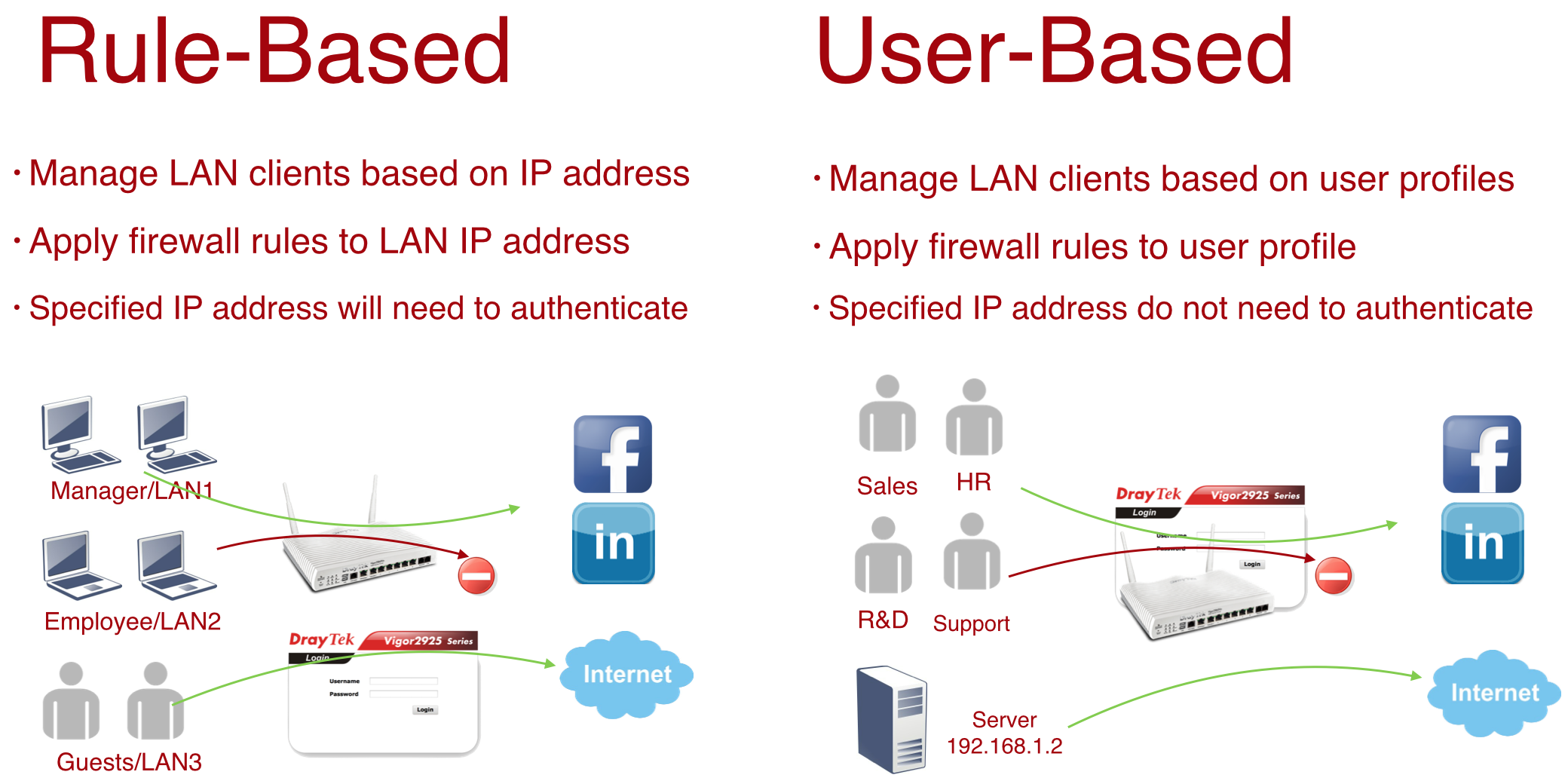
To apply different firewall rules for different LAN clients, Vigor provides two methods, Rule-Based and User-Based. In general, Ruled-Based is management method that Administrator sets different firewall rules for different IP range; and User-Based is a management method that Administrator sets different rules for different user accounts.
There will be 3 parts in this note:
A. Rule-Based
B. User-Based
C. Rule-Based or User-Based?
Before knowing how Rule-Based/User-Based policy management works, let us explain the types of firewall rules to help understanding.
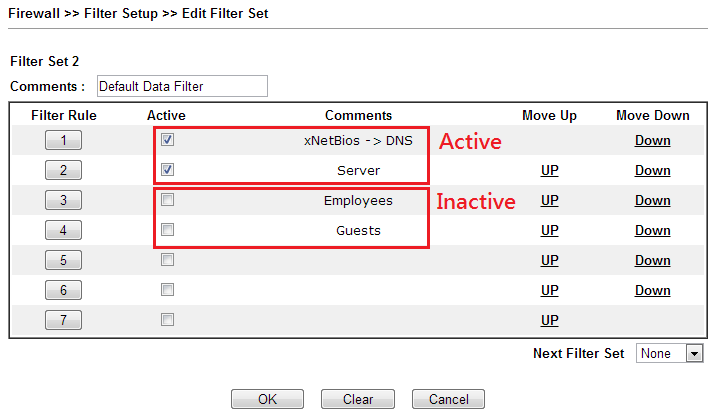
Active Rule: A Filter Rule that is enabled. In Firewall >> Filter Setup, we can see it is ticked to be Active. Active Rules has the first priority that all the packets will be checked if they match the filter rule.
Inactive Rule: A Filter Rule that is NOT enabled. In Firewall >> Filter Setup, we can see it is NOT ticked as Active. If and only if a Filter Rule is inactive can it be set as a policy for a user account.
Default Rule: The rule set in the Firewall >> General Setup >> Default Rule page. In Rule-Based mode, Default Rule is the firewall rule to follow when there is no Active Rule matches. In User-Based mode, Default Rule won't be applied unless it is set as a policy for a user account.
Rule Based
The following figure illustrates how Rule-Based works.
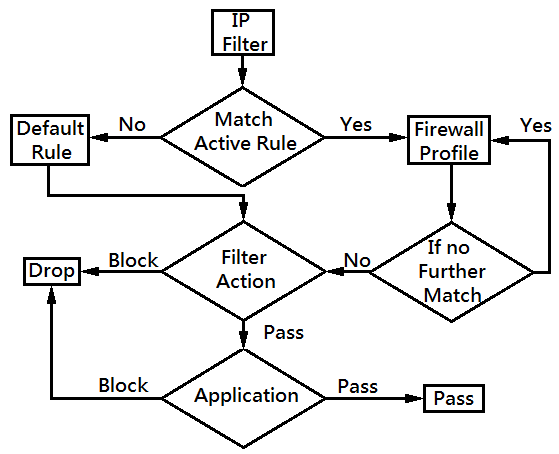
- Active Rule IP filter: When receiving a packet, check if its IP address is in the IP range of the first Active Rule. If yes, apply the filter action. If no, go to the next Active Rule. If the IP address doesn't match any Active Rule, apply Default Rule.
- Filter Action: If the IP address is in the IP range of an Active Rule, there are four possible filter actions:
- Block Immediately: Drop the packet
- Block If No Further Match: Check the rest of the Active Rules in order until it matches one then apply the filter action of that matched Filter Rule. If there's no other Active Rule matched, drop the packet.
- Pass Immediately: Pass and apply applications.
- Pass If No Further Match: Check the rest of the Active rules in order until it matches one then apply the filter action of that matched Filter Rule. If there's no other Active Rule matched, pass and apply filter action.
- Application: If the filter action is “pass” , apply applications such as User Management, URL Content Filter, Web Content Filter or DNS filter, which can be set to block or pass specific content.
In Rule-Base mode, it's which IP range does the packet from determines which firewall rule will be applied. Hence, Administrator can divide the LAN clients into several groups by their IP address, and set different rules for each IP range.
But what if the LAN clients often get different IP address and the administrator still wants to apply specific rule to the specific LAN client? User-Based is the solution!
User Based
The following figure illustrate how User-Base works.
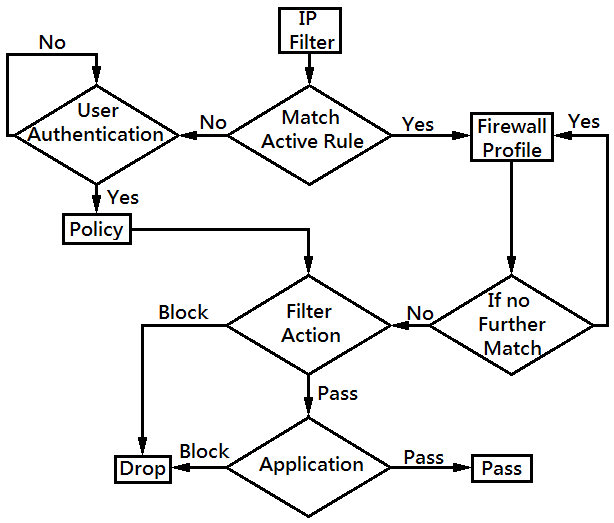
- Active Rule IP filter: When receiving a packet, check if the IP address matches any Active Rule IP range. If yes, follow the procedure as Rule-Based in Part A. If no, User Authentication will be required.
- User Authentication: If none of the Active Rules is matched, request User Authentication and apply the Policy for that user account. Then follow the procedure similar to Ruled-Based.
Policy IP filter: First, check if the IP address is in the Policy IP range. If no, drop the packet. If yes, apply its filter action.
Note: If Policy is set for a specific IP range, the users won't be able to access the Internet if their IP address doesn't match the policy, even if they log in with the correct username and password.
- Filter Action: If the IP address is in the IP
range of the policy, apply its filter action. There are two
possible actions:
- Block Immediately/Block If No Further Match: Drop packet
Pass Immediately/Pass If No Further Match: Pass and apply applications.
Note: Since each user profile can only select one policy, Block/Pass If No Further Match has the same effect as Block/Pass Immediately.
- Application:If the filter action is “pass”, apply applications such as User Management, URL Content Filter, Web Content Filter or DNS filter, which can be set to block or pass specific content.
In User-Base mode, if the packet doesn't match any Active Rule, then the LAN client will need User Authentication to access the Internet. Administrator can set different rules for different user accounts. So even if the LAN clients often get different IP address, just request them to log in, and they will still have to follow the firewall policy attached to their user account.
Rule-Based or User-Based
In summary, Vigor provide two different methods for user management. Ruled-Based is based on the LAN client's IP, and User-Based is based on the user account. So how to choose between Rule-Based or User-Based mode?
For Administrator who is used to mange LAN clients by their IP address, we would recommend using Rule-Based mode. But please note that the firewall rules may not be applied as expected if the LAN clients gets a different IP address, so “Bind IP to MAC”, setting static IP addresses, or enabling multiple LAN subnets for different LAN cleints may be required.
For Administrator who don't want to restrict LAN clients to a fixed IP address, we would recommend User-Based mode. In this way, which user account does the LAN client log in with matters more than which IP address they are from. But please note that with this configuration, the LAN clients will need to log in every time they connects to the Internet, and this may be a little inconvenient.
Published On:2020-07-15
Was this helpful?
