Some users report they create L2TP over IPsec or IKEv2 EAP VPN but cannot run speed tests over the VPN tunnel. After some checking, we find the packets are blocked by the UDP Flood Defense function on the router in front of it.
The UDP Flood Defense function will drop UDP packets while receiving lots of UDP packets with the same source port in a short time, and the default UDP flood threshold is 2000 packets in 60 seconds.
When the VPN client is behind NAT, the IPsec VPN will use NAT-Traversal to pass through the NAT. That means the VPN client will add a UDP header with port 4500 on the packets to the remote VPN network. While running a speed test over the L2TP over IPsec VPN tunnel, the LAN client sends many UDP packets, and these packets will be regarded as the UDP Flood traffic by the NAT Router if it enables DoS Defense.
We may disable the UDP Flood Defense function, or increase the threshold of the UDP Flood for allowing the L2TP over IPsec VPN client in LAN to test the speed.
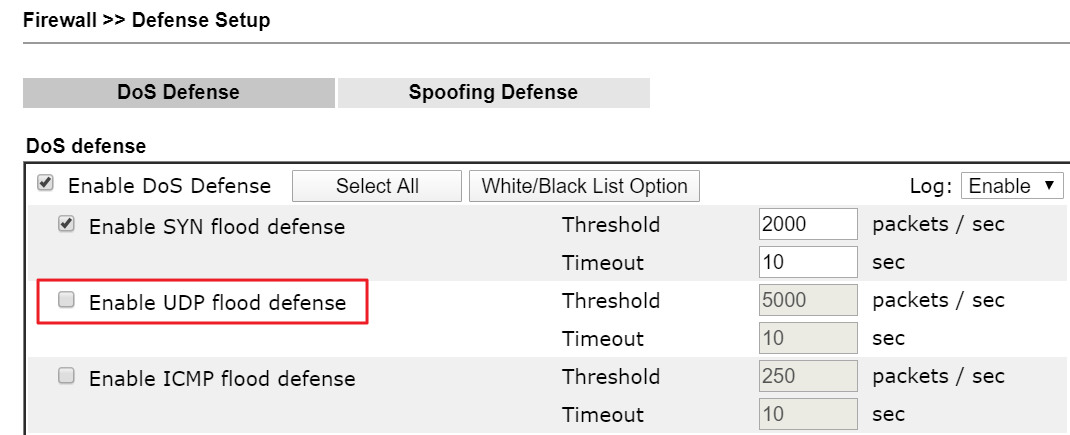
Note, not only the NAT-T IPsec VPN but also other services that use UDP protocol, such as DNS, SIP may be affected by the UDP Flood Defense function. While you have the servers in Vigor Router's LAN, please remember to disable the UDP flood defense option or add the server's IP into the White List.
Published On:2020-04-15
Was this helpful?
