VigorAP support internal radius feature, so they can act as authentication servers in 802.1X authentication. Also, we could select two RADIUS EAP Type: PEAP or EAP-TLS for different situation. This document introduces how to set up VigorAP to be a RADIUS server.
1. Enable RADIUS server feature in RADIUS Setting >> RADIUS server
2. Create User profiles: Type username and password then press the Add button to create the account.
3. Set up Authentication Client: Authentication Clients are the hosts who will have the permission to send 802.1X authentication packets to the VigorAP. Type Client IP and Secret Key then press the Add button to add a new client.
4. Now the VigorAP is a RADIUS server. For the RADIUS client (e.g., an 802.1X authenticator) which would like to use the VigorAP as RADIUS server, need to enter the IP address of VigorAP and Secret Key set in step 3.
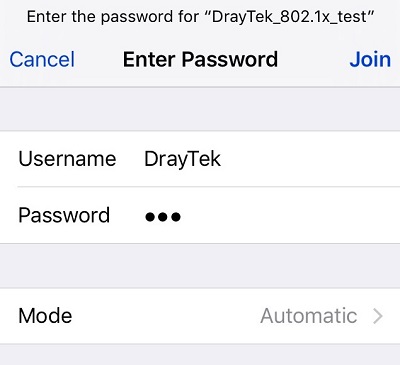
5. After the above configuration, when client devices connect to RADIUS client (the authenticator) and attempt to join the network, they will be asked to provide the credentials, which will be forwarded to the VigorAP for verification, and the credentials will be determined valid if they match the username and password set in step 2.
Use EAP-TLS Type
If the client requires server authentication for 802.1X authentication (e.g., Windows PC), we may use EAP-TLS Type, and create a RootCA in RADIUS server >> Certificate Management to obtain the server certificate for client authentication. For detailed instructions, see 802.1X Authentication with Self-Generated Server Certificate

Published On:2018-07-13
Was this helpful?
