This document introduces how to use the IPsec Multiple SA feature to access more than one remote subnets over one VPN profile. Multiple SA is for connecting to a non-DrayTek VPN server with multiple subnets. When connecting to another Vigor Router with multiple subnets, multiple IPsec SA is not required, we should use the "More" Remote Subnet feature to add additional routes over the same tunnel.
Configuring DrayTek router as a VPN Server
1. Go to VPN and Remote Access >> IPsec General Setup, and enter General Pre-Shared Key.
2. Go to VPN and Remote Access >> LAN to LAN, and click on an index number to create a new IPsec profile.
3. Set configurations of IPsec profile.
- Enter a Profile name, and check Enable this profile.
- Choose Dial-In.
- Choose "IPsec Tunnel" for Allowed VPN Type
- Enter Remote Network IP.
- Click More Remote Subnet.
- Check Create Phase2 SA for each subnet (IPSec).
- Enter second Local Network and Remote Network, and click Add.
- Click OK to save the profile.
Configuring DrayTek router as a VPN Client
1. Go to VPN and Remote Access >> LAN to LAN, and click on an index number to create a new IPsec profile.
2. Set configurations of IPsec profile.
- Enter a Profile name, and check Enable this profile.
- Choose Dial-Out.
- Choose "IPsec Tunnel" for VPN Server
- Enter the Server IP/Hostname.
- Enter Pre-Shared Key.
- Enter Remote Network IP.
- Click More Remote Subnet.
- Check Create Phase2 SA for each subnet (IPSec).
- Enter second Local Network and Remote Network, and click Add.
- Click OK to save the profile.
Note: If there is more than 1 SA, please check Always-on option.
Check VPN connectivity
Go to VPN and Remote Access >> Connection Management and click Dial on VPN client.
Then we will see 2 VPN tunnels are established as per VPN network configuration.
Note: Only 1 Local network can be used on legacy models.
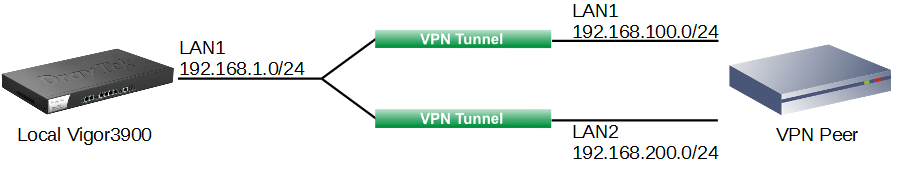
Case 1: Vigor3900 has one local network while the VPN Peer has two
In this example, Vigor3900's LAN network is 192.168.1.0/24. VPN Peer's LAN1 network is 192.168.100.0/24 and LAN2 is 192.168.200.0/24.
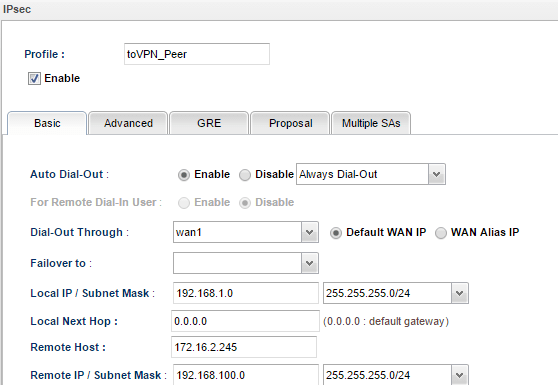
1. In the Basic tab, we may configure Vigor3900's LAN network (192.168.1.0/24) as Local IP/Subnet Mask and VPN Peer's LAN1 network (192.168.100.0/24) as Remote IP/ Subnet Mask.
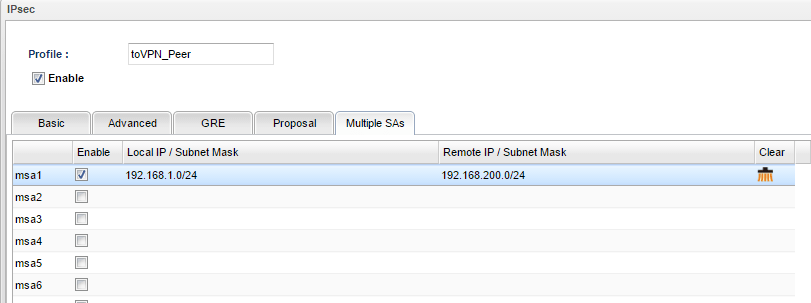
2. In Multiple SA tab, input Vigor3900's LAN network for Local IP/ Subnet Mask again and VPN Peer's LAN2 network for Remote IP/ Subnet Mask.
3. We need to configure the similar Multiple SA setting or create two IPsec VPN dial-in profiles on the remote site Vigor3900.
4. During IPsec connection establishment, Vigor3900 will create two IPsec SA. One is to encrypt the data between network 192.168.1.0/24 and 192.168.100.0/24. The other is to encrypt the data between network 192.168.1.0/24 and 192.168.200.0/24.
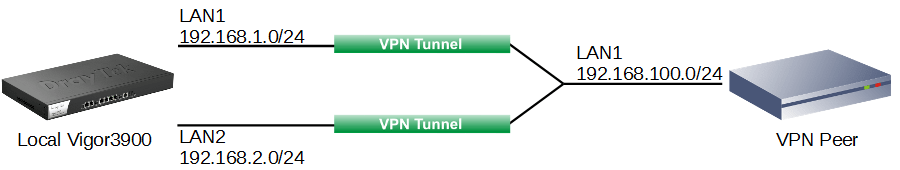
Case 2: Vigor3900 has two local networks while the VPN Peer has one
In this example, Vigor3900's LAN1 network is 192.168.1.1/24, and LAN2 is 192.168.2.1/24. VPN Peer's LAN network is 192.168.100.1/24.
1. In Basic Tab, we may configure Vigor3900's LAN1 network as Local IP/ Subnet Mask, and VPN Peer's LAN network (192.168.100.0/24) as Remote IP/ Subnet Mask.
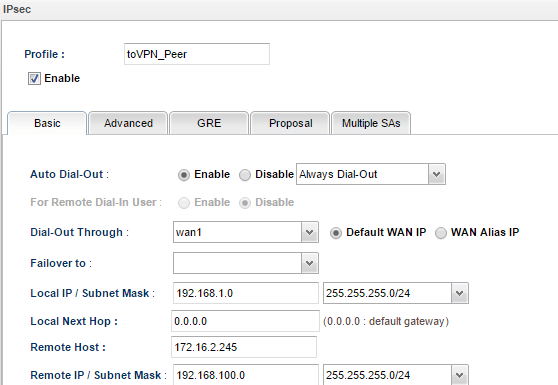
2. Then in Multiple SA tab, input Vigor3900's LAN2 network and VPN Peer's LAN network.
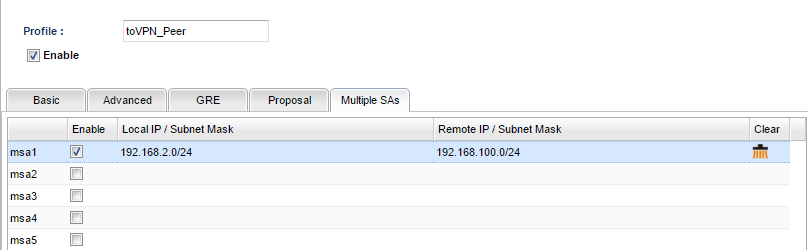
3. We need to configure the similar Multiple SA setting or create two IPsec VPN dial-in profiles on the remote site Vigor3900.
4. During IPsec connection establishment, Vigor3900 will create two IPsec SA. One is to encrypt the data between network 192.168.1.0/24 and 192.168.100.0/24. The other is to encrypt the data between network 192.168.2.0/24 and 192.168.100.0/24.
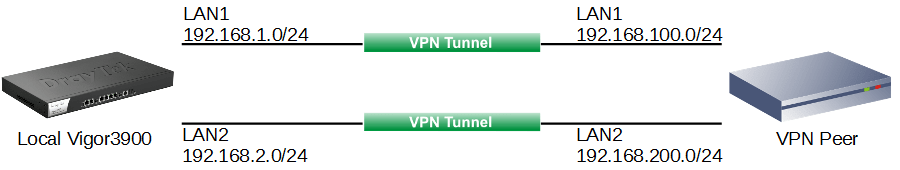
Case 3: Both Vigor3900 and the VPN Peer have two local networks
In this example, Vigor3900's LAN1 network is 192.168.1.0/24, and LAN2 is 192.168.2.0/24. VPN Peer's LAN1 network is 192.168.100.0/24 and LAN2 network is 192.168.200.0/24.
1. In the Basic tab, we may configure Vigor3900's LAN1 network as Local IP/ Subnet Mask, and VPN Peer's LAN1 network (192.168.100.0/24) as Remote IP/ Subnet Mask.
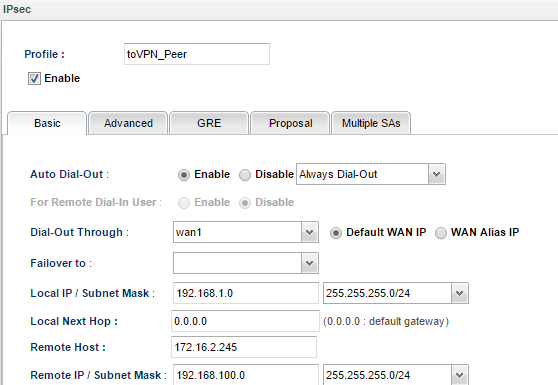
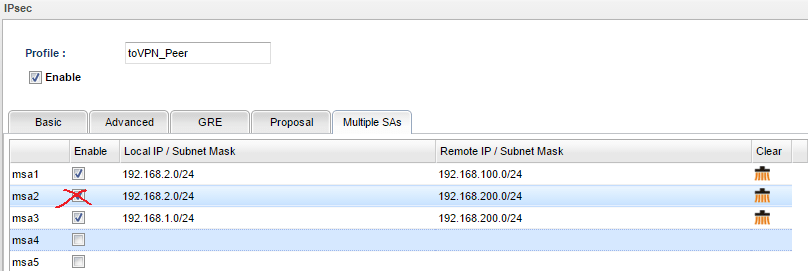
2. In Multiple SA tab, input the following three settings:
- Vigor3900's LAN2 network to VPN Peer's LAN1 network
- Vigor3900's LAN2 network to VPN Peer's LAN2 network
- Vigor3900's LAN1 network to VPN Peer's LAN2 network
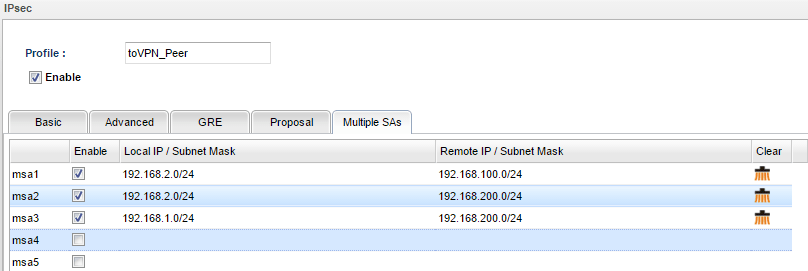
3. During the IPsec connection establishment, Vigor3900 will create 4 IPsec SAs. One is to encrypt data between network 192.168.1.0/24 and 192.168.100.0/24; and the rest of them are to encrypt data between network 192.168.1.0/24 and 192.168.200.0/24, network 192.168.2.0/24 and 192.168.100.0/24, and between network 192.168.2.0/24 and network 192.168.200.0/24.
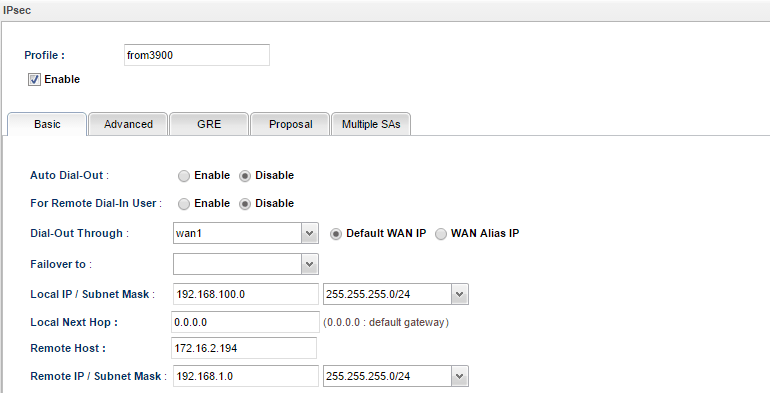
4. Of course, VPN Peer should have corresponding configurations. Take another Vigor3900 acting as VPN Peer for example. In the Basic tab, we may configure LAN network (192.168.100.0/24) as Local IP/ Subnet Mask, and the other Vigor3900's LAN network (192.168.1.0/24) as Remote IP/ Subnet Mask.
5. Then in Multiple SA tab, input the following three settings:
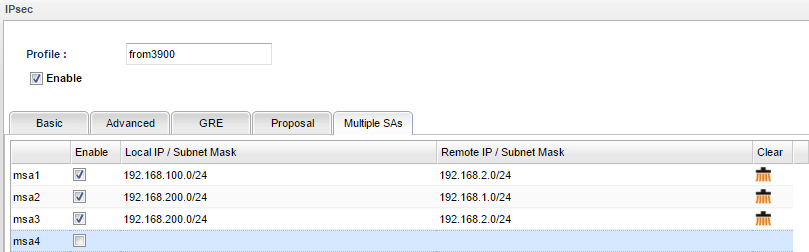
6. After the above configurations, we should see 4 IPsec connections between the two routers. The data transferring between different networks are encrypted by four different IPsec SAs.
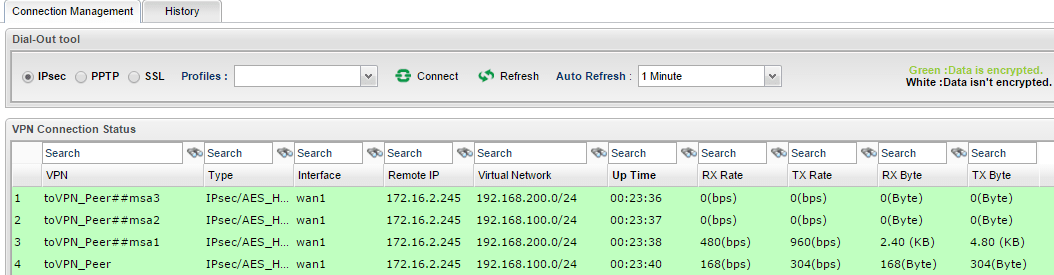
7. And what could we do if we don't want local network 192.168.2.0/24 to access remote network 192.168.200.0/24? Just remove msa2 in Multiple SAs tab!
Published On: 2016-05-18
Was this helpful?
