DMZ, which stands for Demilitarized Zone, is an additional layer of security between the WAN and the LAN. A router with a DMZ subnet will allow access to the DMZ from the WAN while having the LAN still protected by the firewall. The most common application of DMZ is to allow servers such as mail servers, HTTP/HTTPS web servers and FTP servers, to provide service to the hosts on WAN.
On Vigor routers, there are two ways to set up DMZ: DMZ host and DMZ subnet. Setting up a DMZ host will open a single host completely to the WAN, and all packets will be forwarded to this single host, unless:
- The packets match port redirection or open ports rules
- The packets destined to ports that the router itself is actively listening. (For example, if WAN management is enabled on the router on telnet and HTTP ports, inbound packets to ports 23 and 80 will be intercepted by the router).
The DMZ host is easy to set up and convenient to use. However, because the DMZ host is on the same subnet as other LAN devices, if an attacker breaches the security of this host, he or she may be able to compromise the security of the entire LAN.
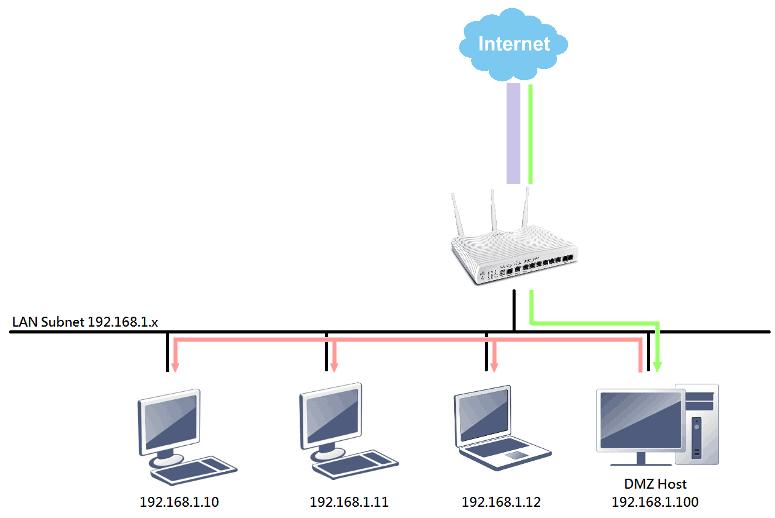
In the illustration above, the green arrow indicates normal usage of the DMZ host, where users on the Internet can access the DMZ host using the WAN IP address of the router. If an attacker breaches the security of the DMZ host, the attacker may gain unauthorized access to other hosts on the same subnet, indicated by the red arrows.
We can avoid this type of threats can by using the DMZ subnet instead. Since it's an independent subnet, the DMZ host and other LAN subnet are isolated. Therefore, if an attacker breaks into a host on the DMZ subnet, he or she cannot access the other LAN subnets.
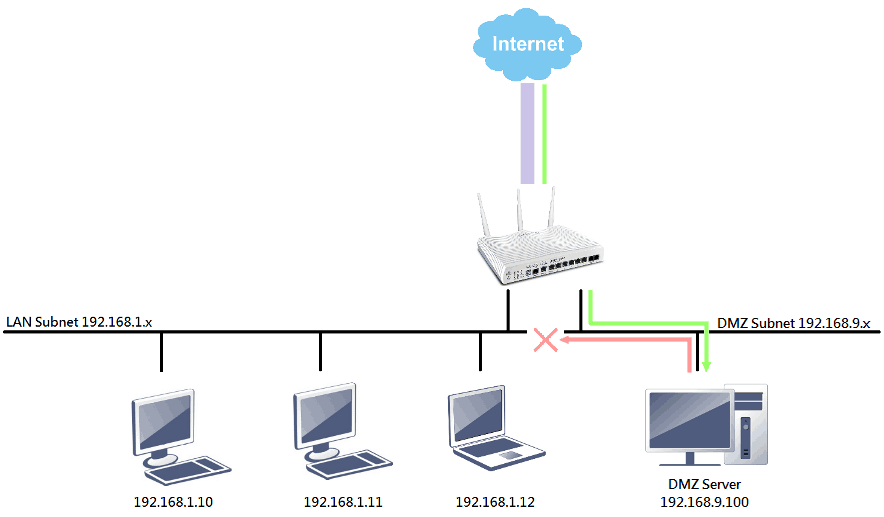
To allow WAN hosts to access servers on the DMZ subnet, the network administrator must set up Port Redirection or Open Ports rules to those servers. Also, to allow users on LAN subnets to access servers on the DMZ subnet, inter-LAN routing must be enabled, and firewall rules must be set up, as shown below.
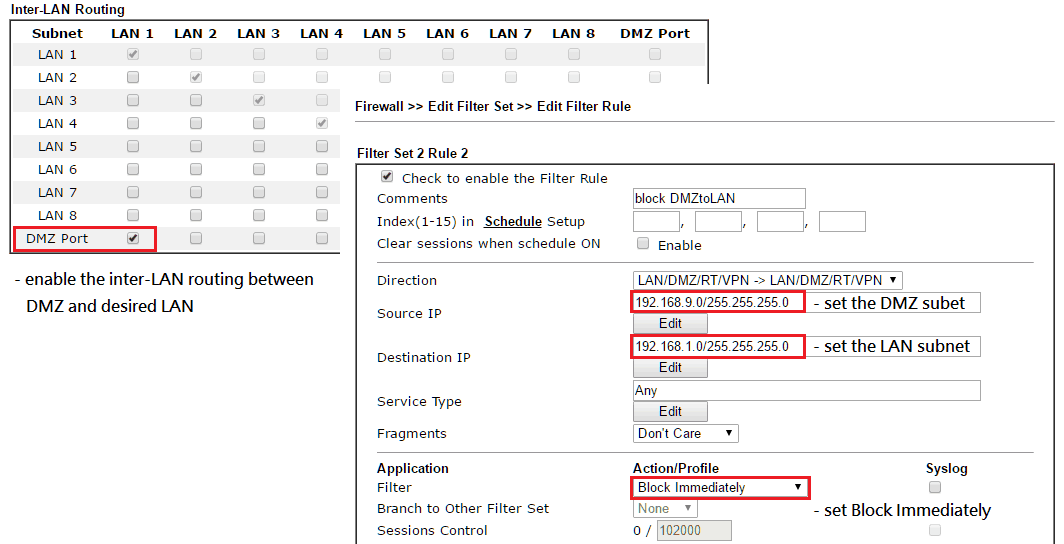
The router will then allow hosts on the LAN subnets to access the DMZ subnet but prevent hosts on DMZ subnet from initiating sessions to the LAN subnets. The rule protects both the router and the rest of the LAN from unauthorized access from the DMZ.
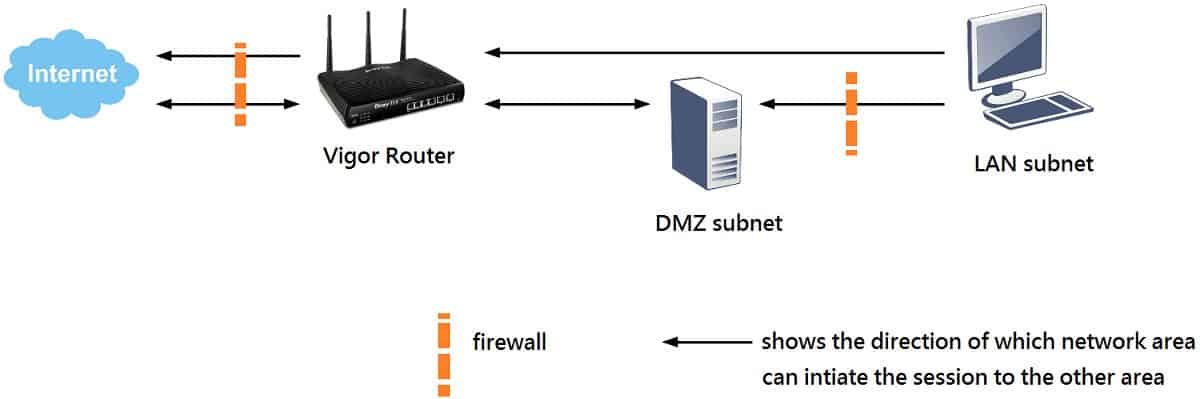
Even though the configuration of the DMZ subnet is a bit more complicated than that of the DMZ host, the result of having a more secure networking environment makes it worthwhile.
The dedicated DMZ port on Vigor3220

On most Vigor routers with multiple LAN ports, the router will set aside one of the LAN port as the DMZ port when the DMZ subnet is enabled. The Vigor3220 series of routers, however, are equipped with one LAN port, plus a dedicated DMZ port that is always enabled.
Published On:2017-02-14
Was this helpful?
